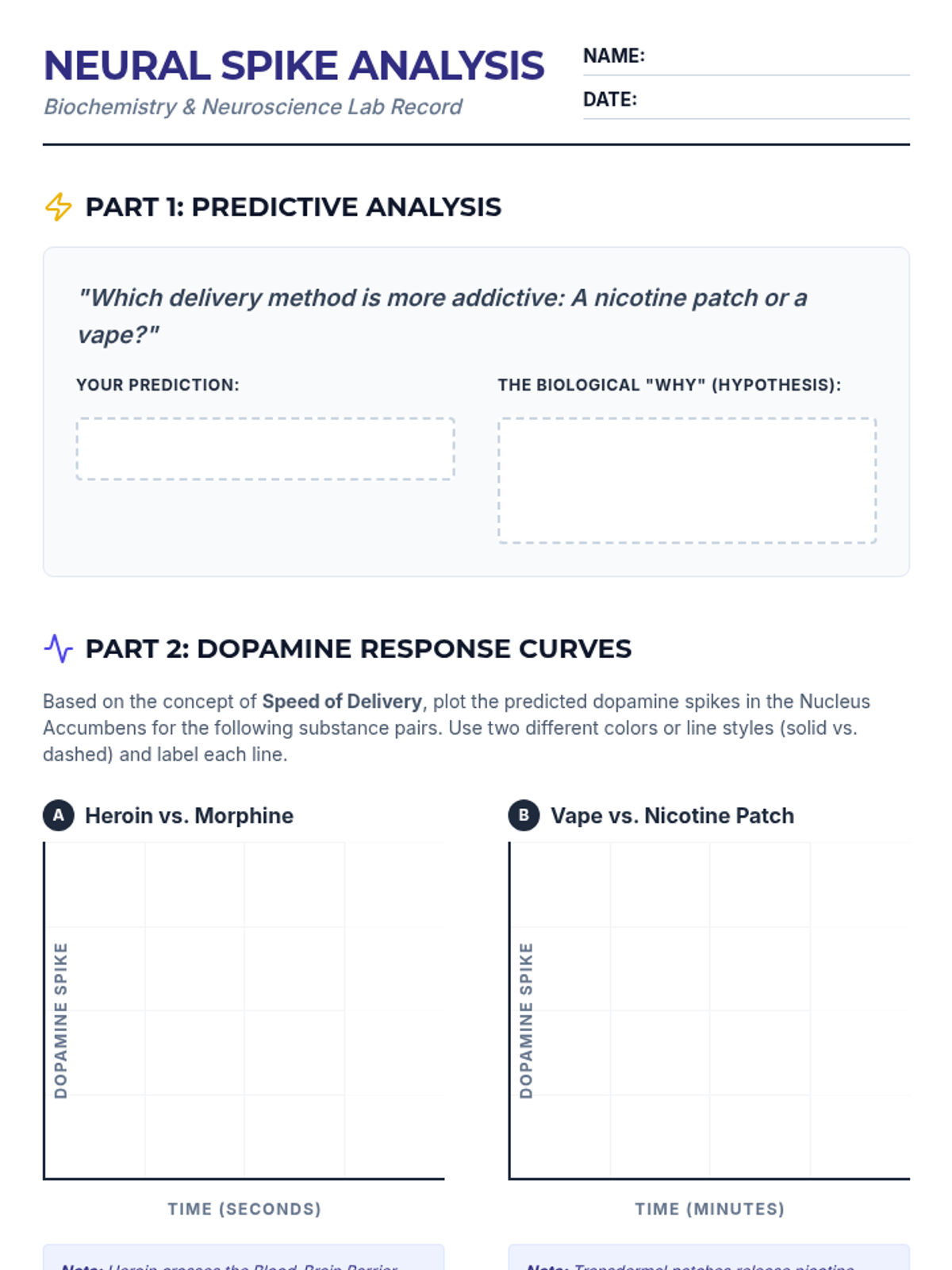
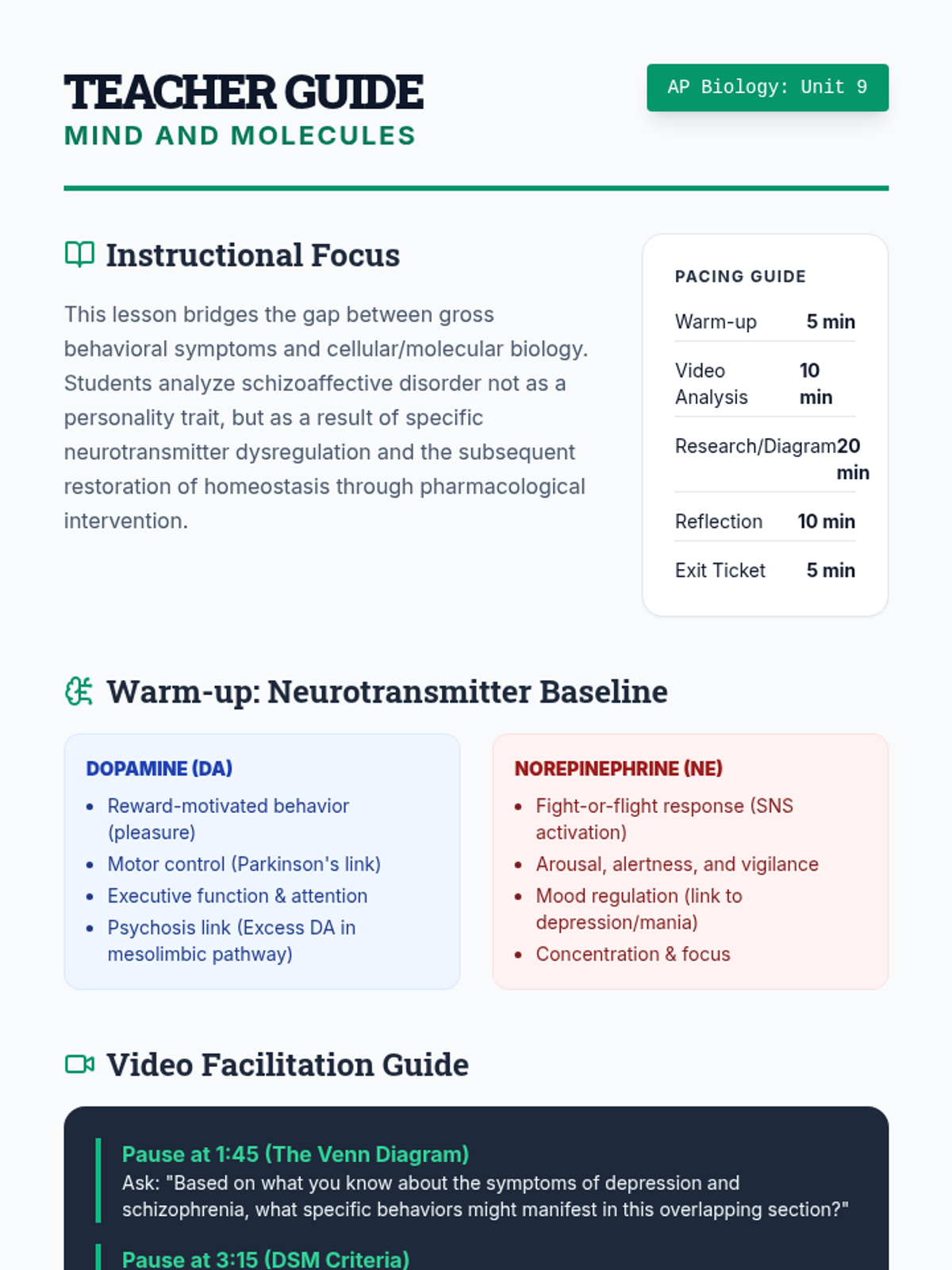
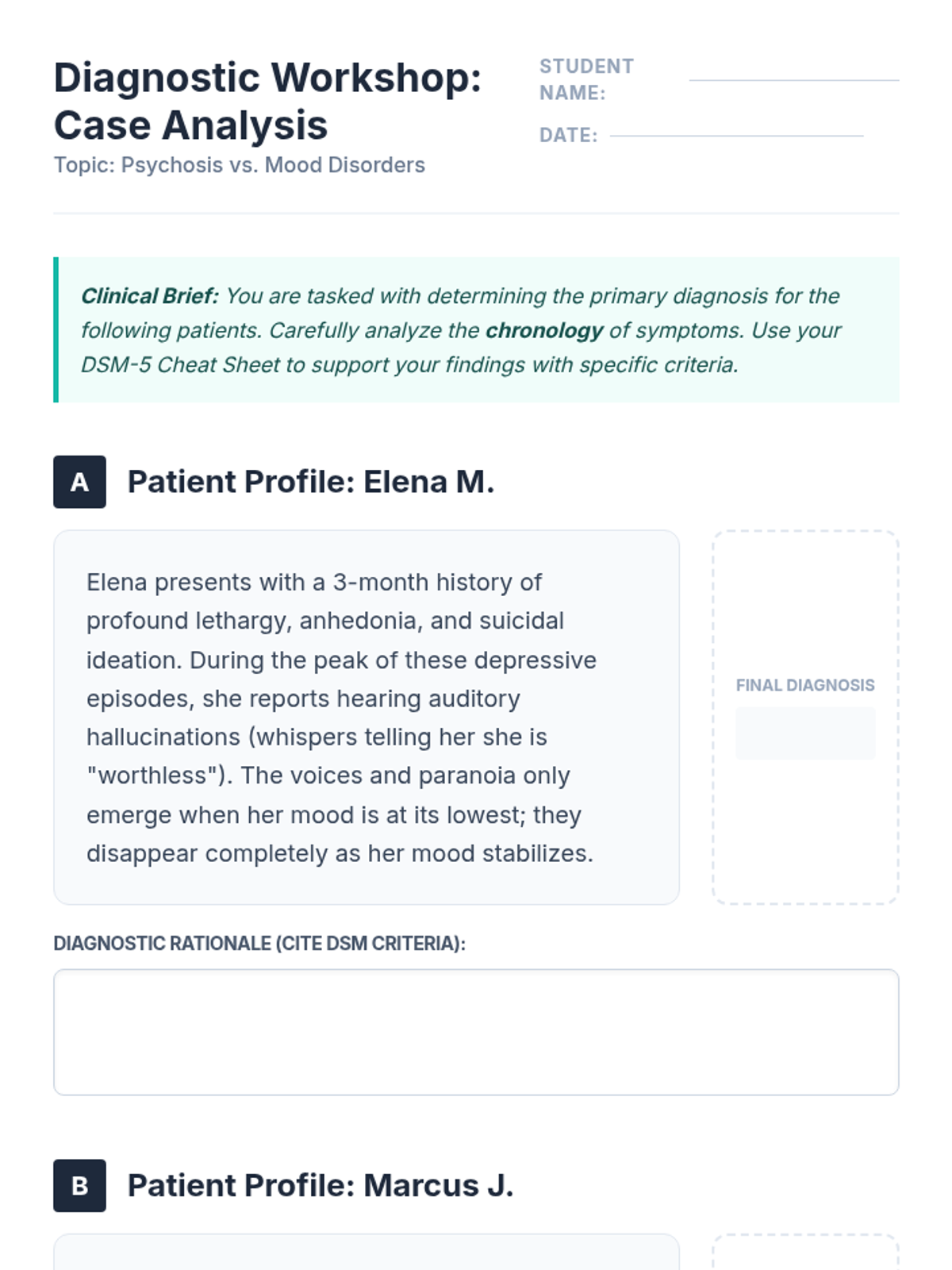
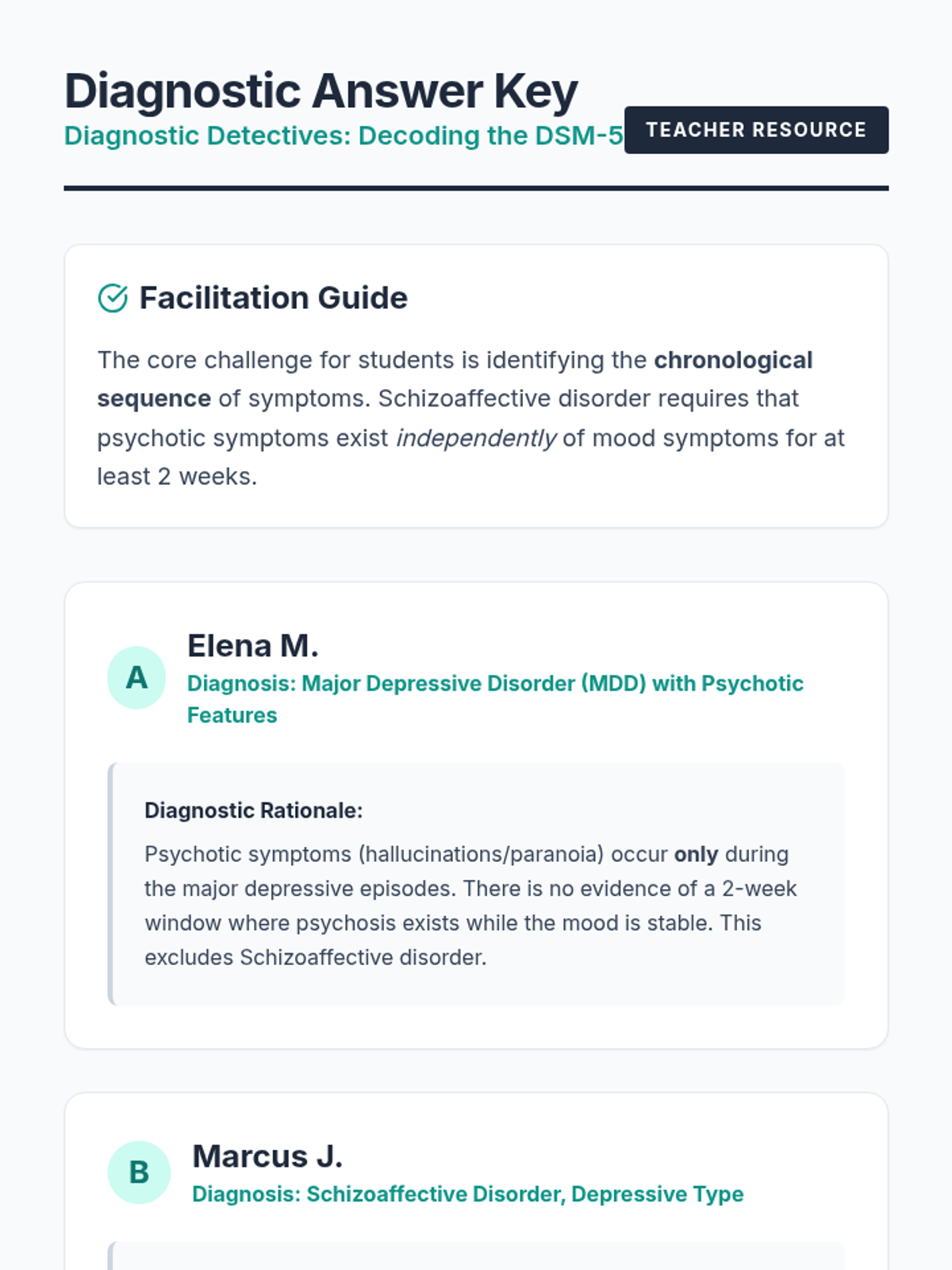
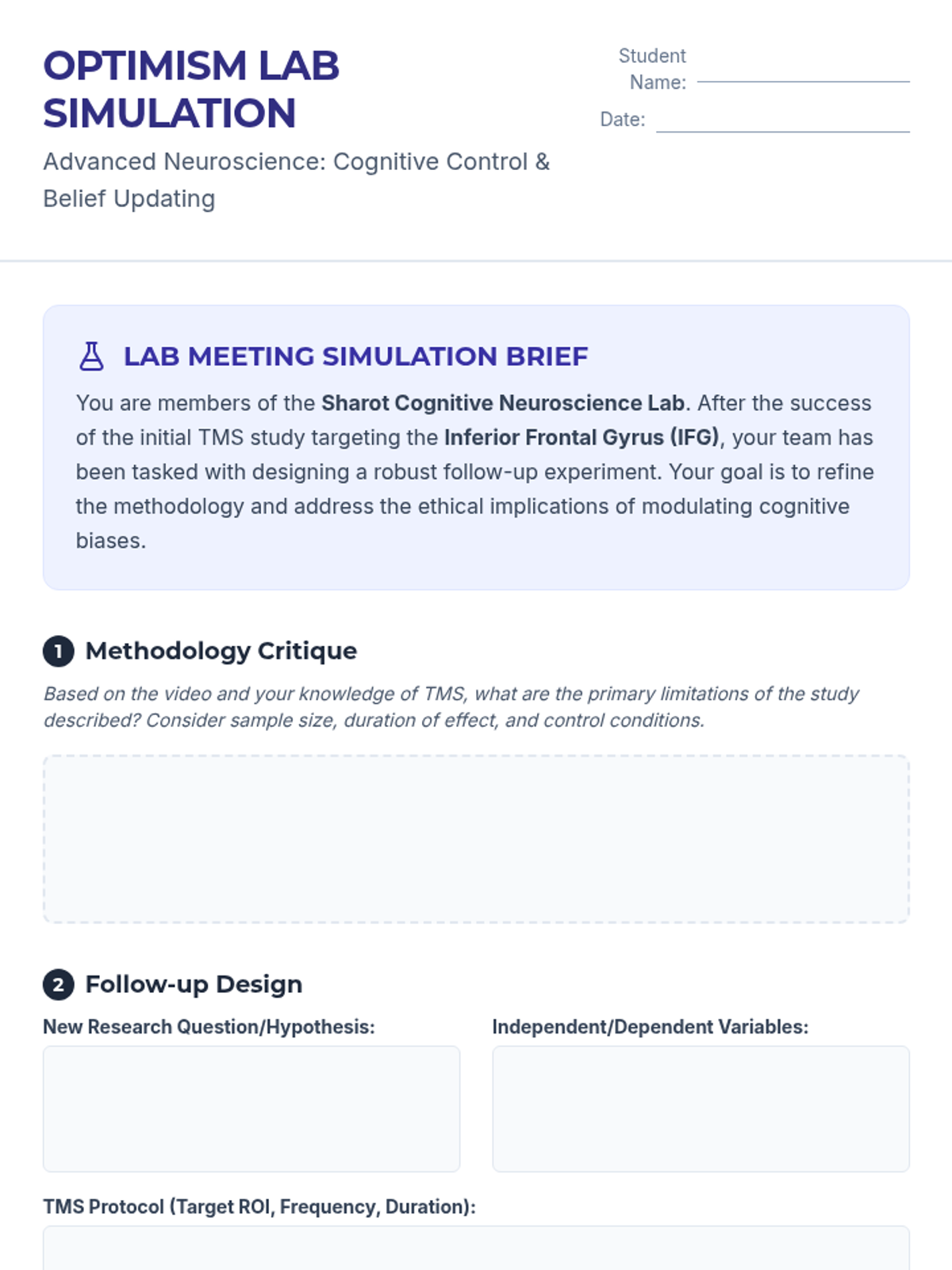
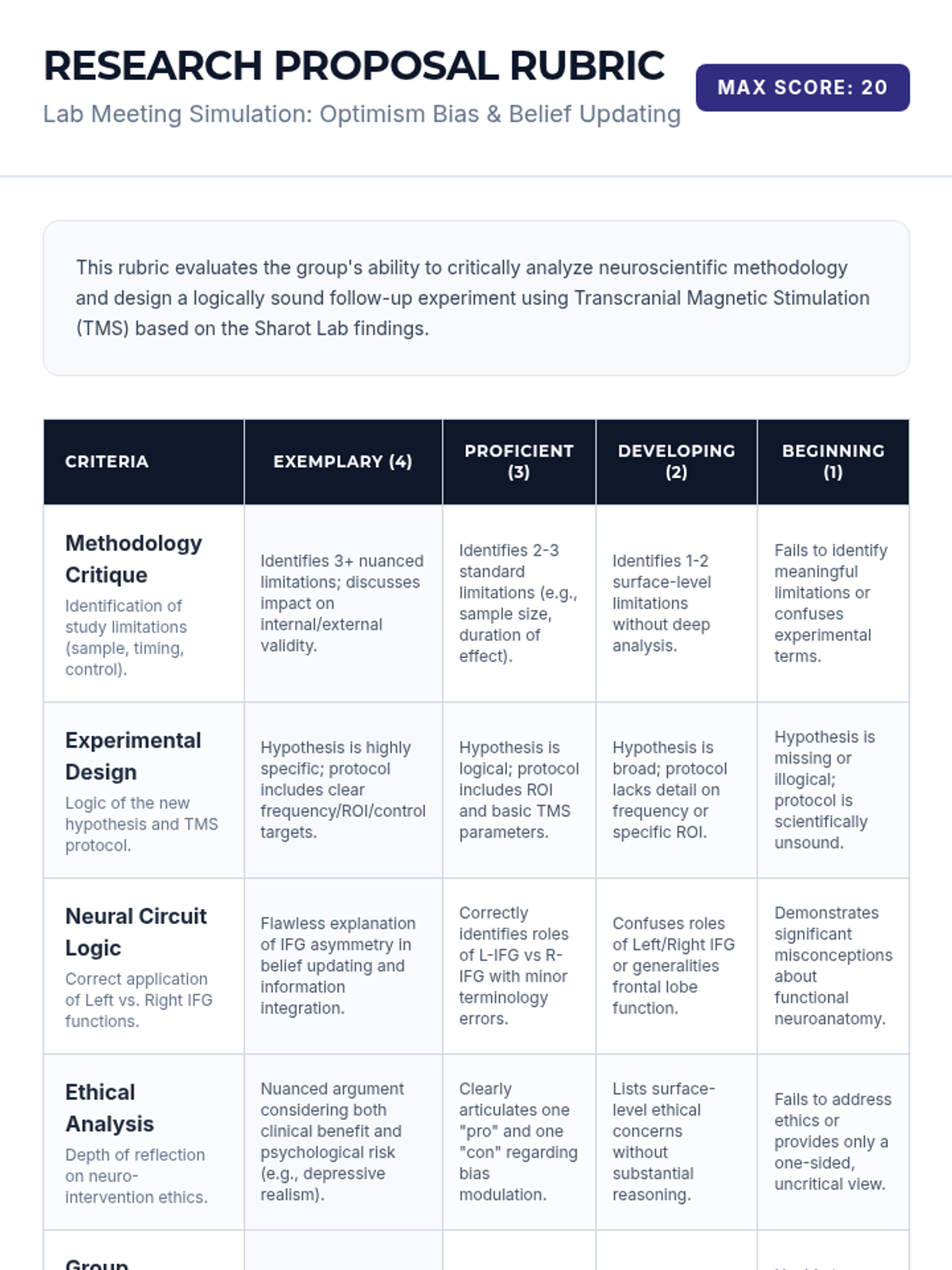
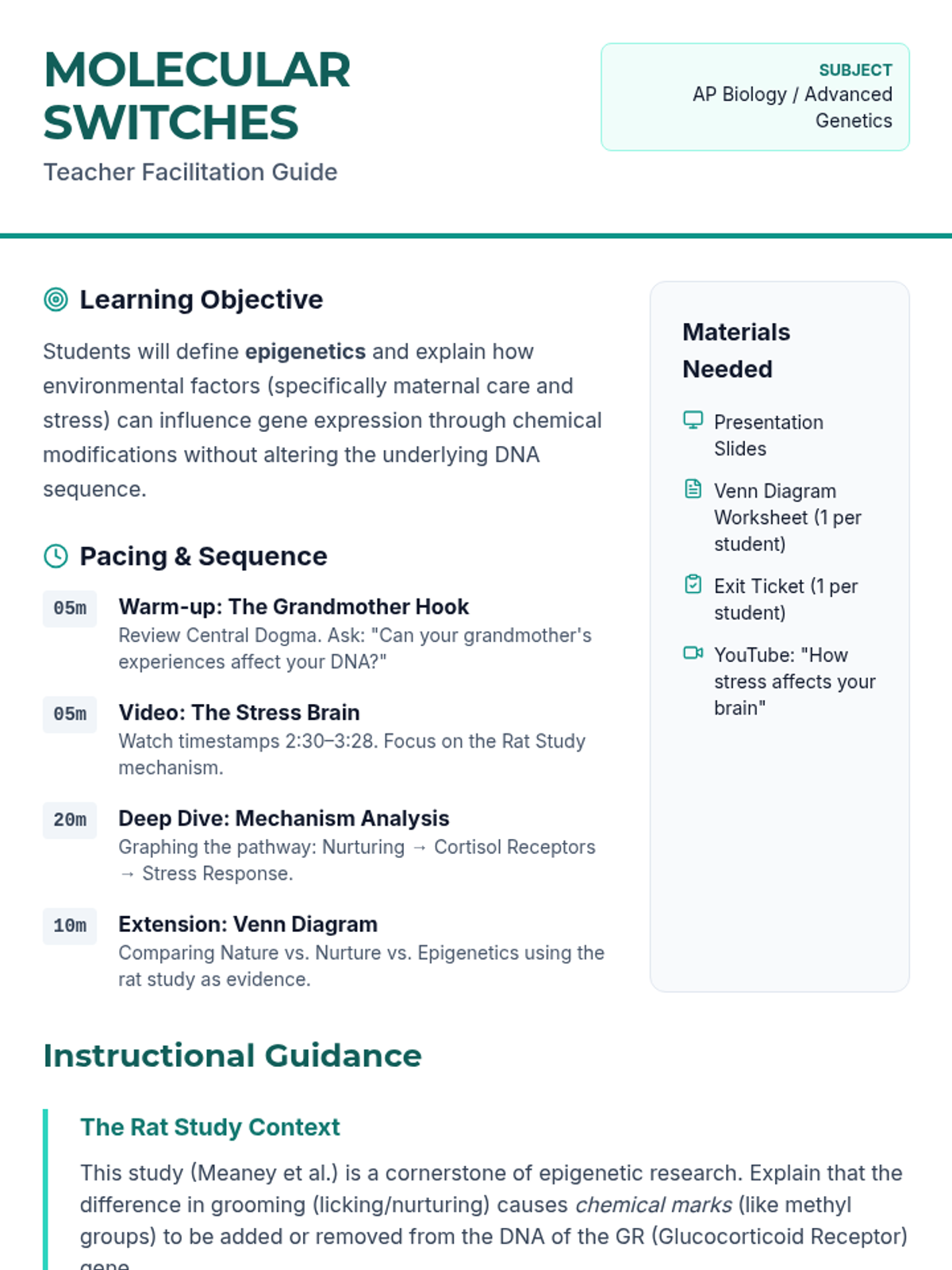
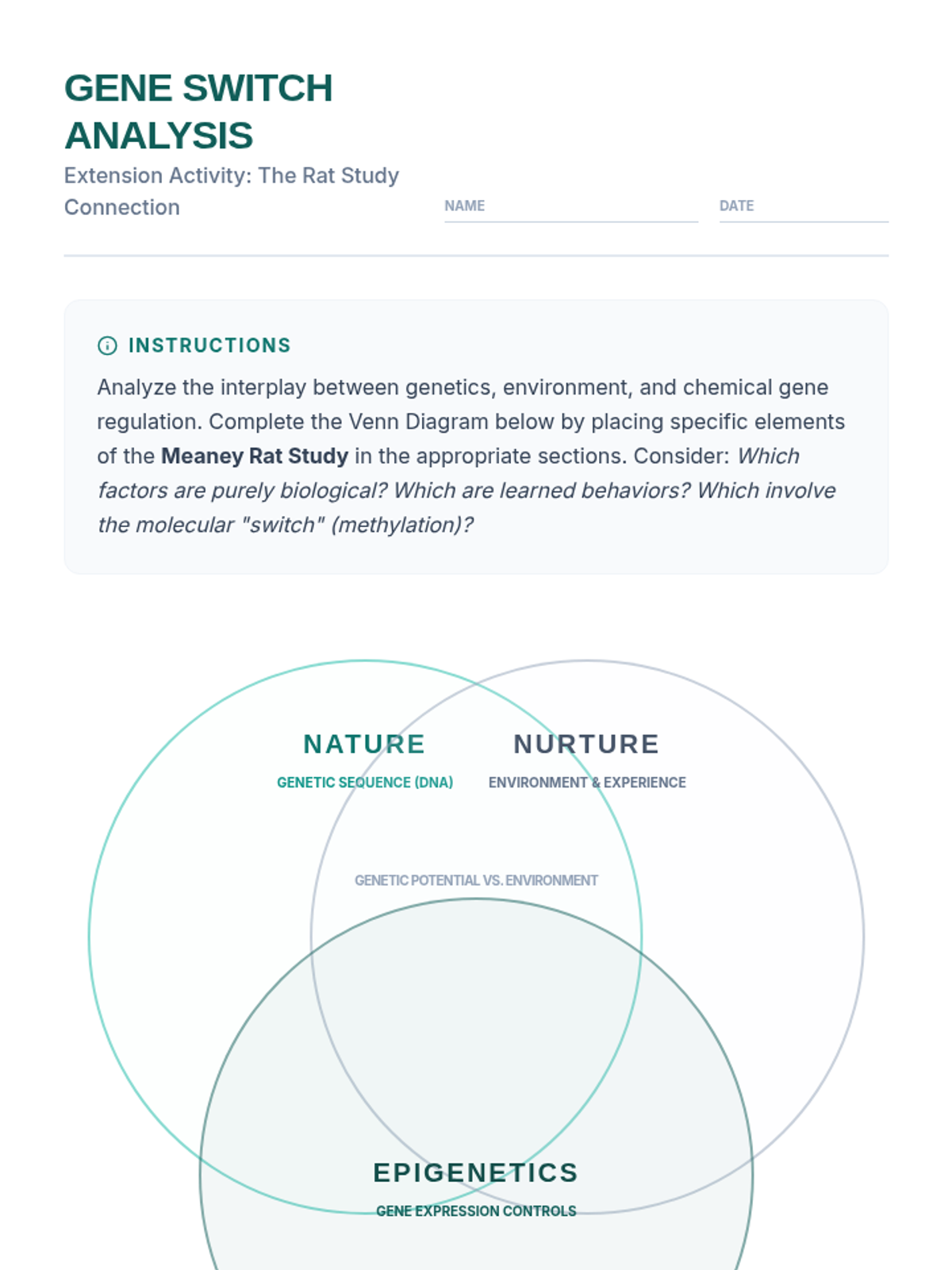
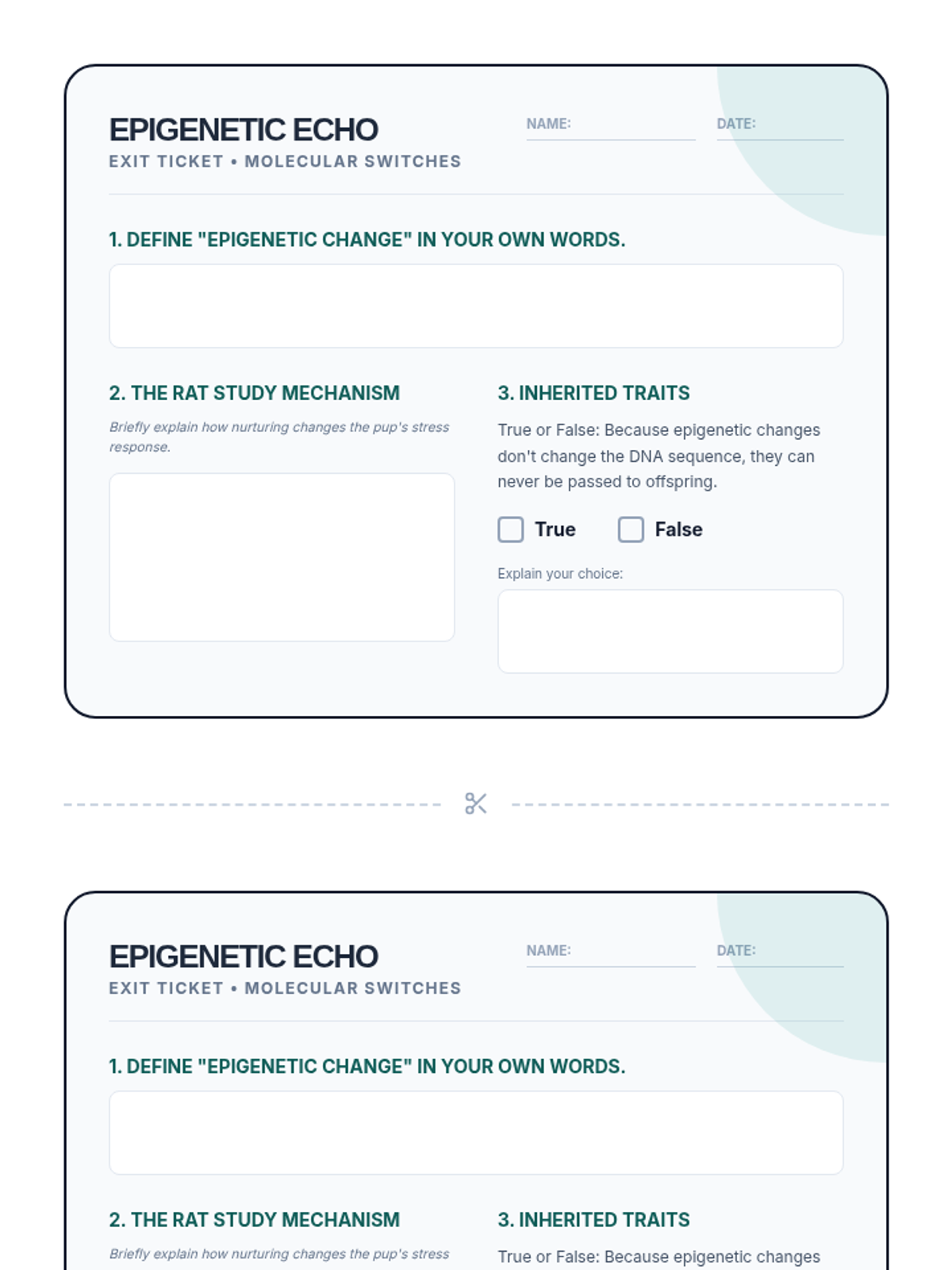
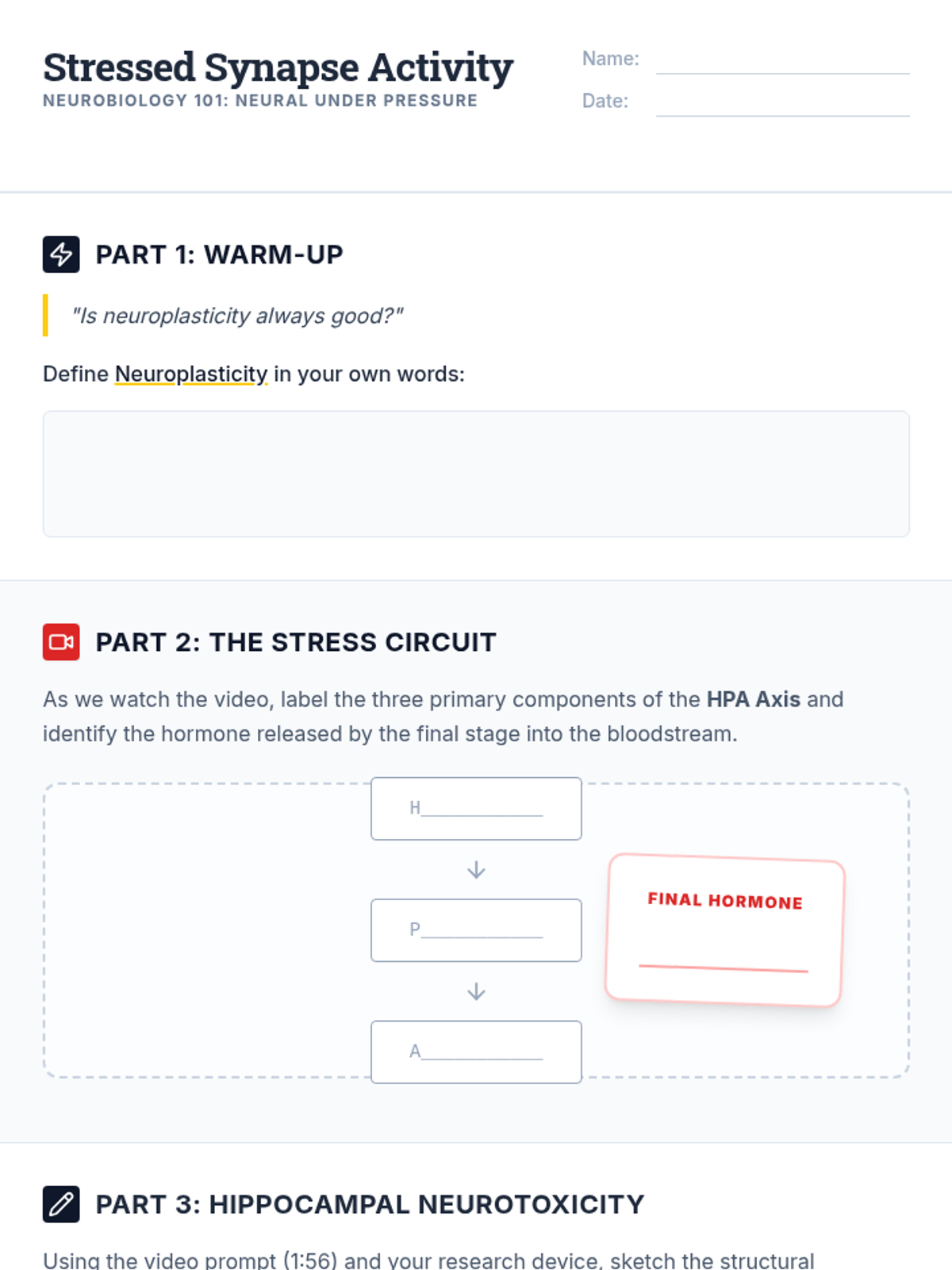
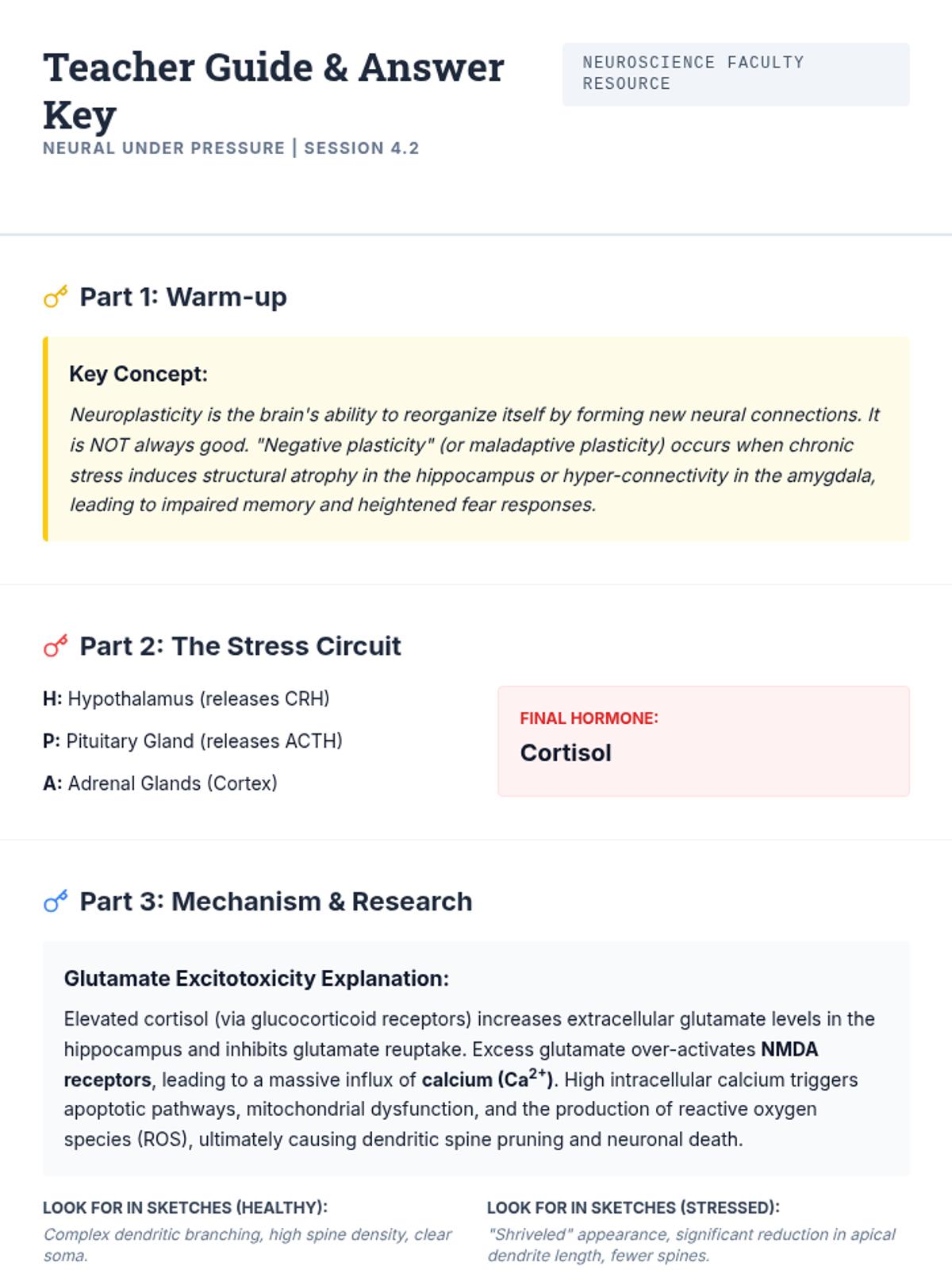
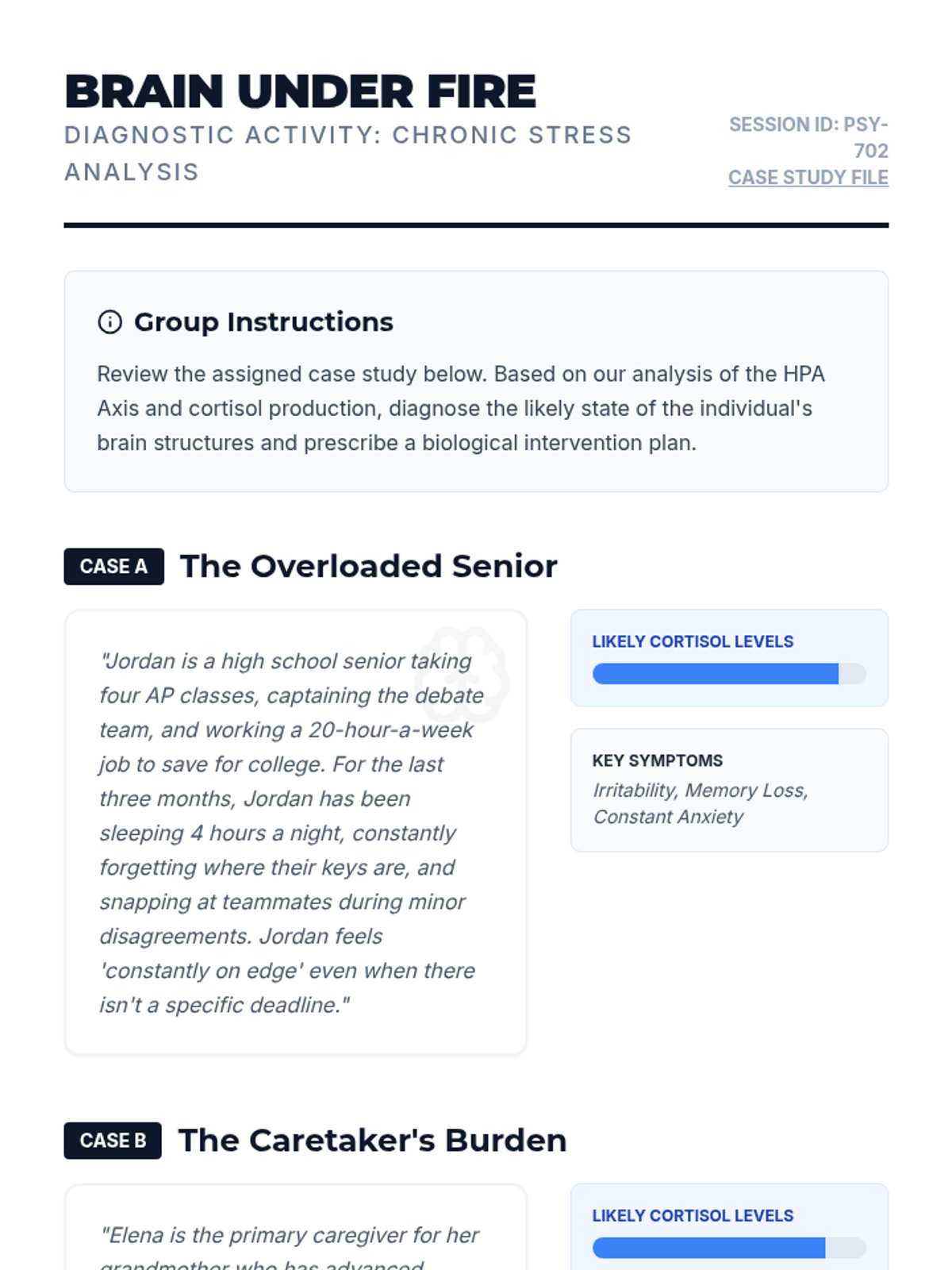
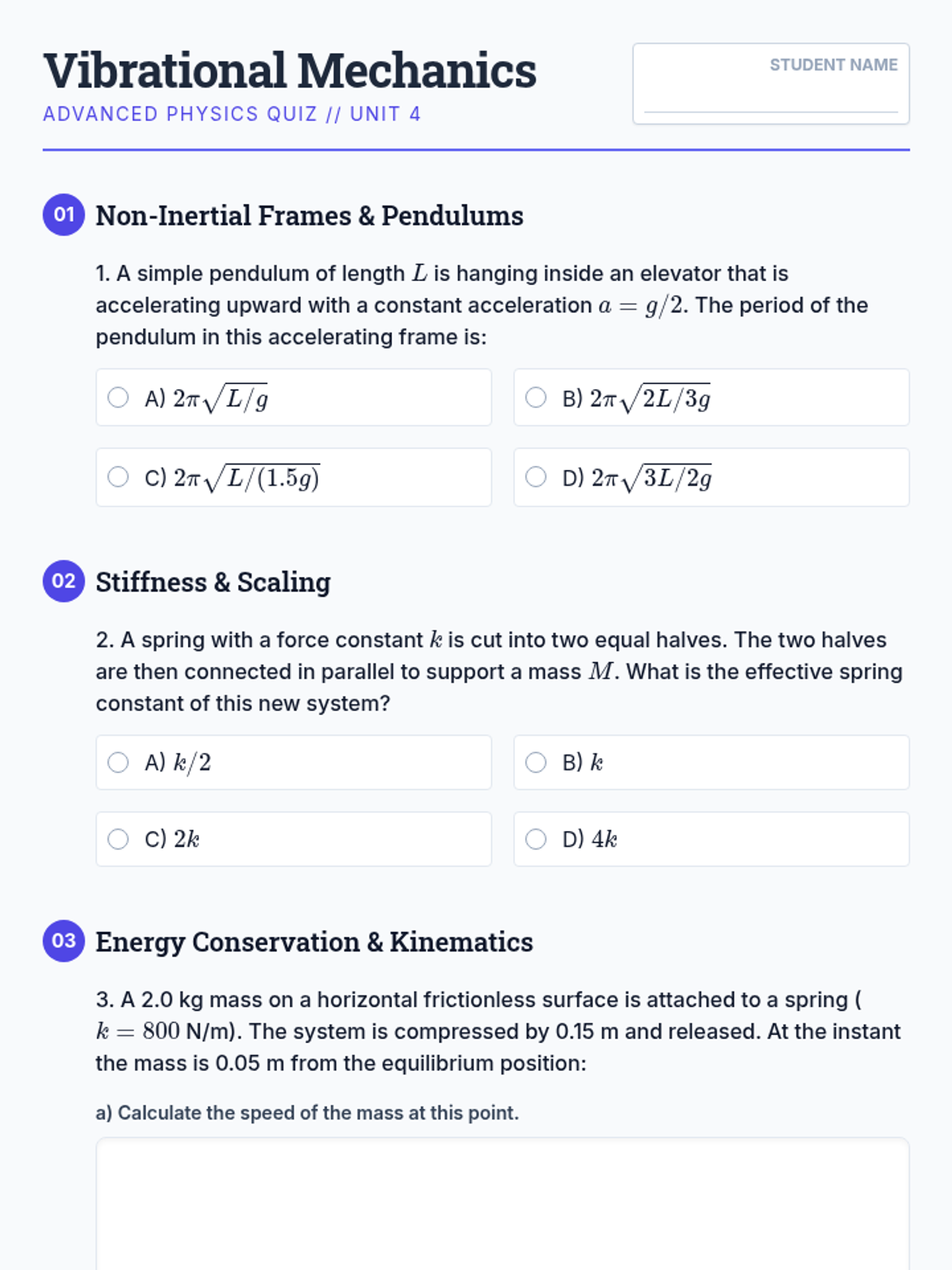
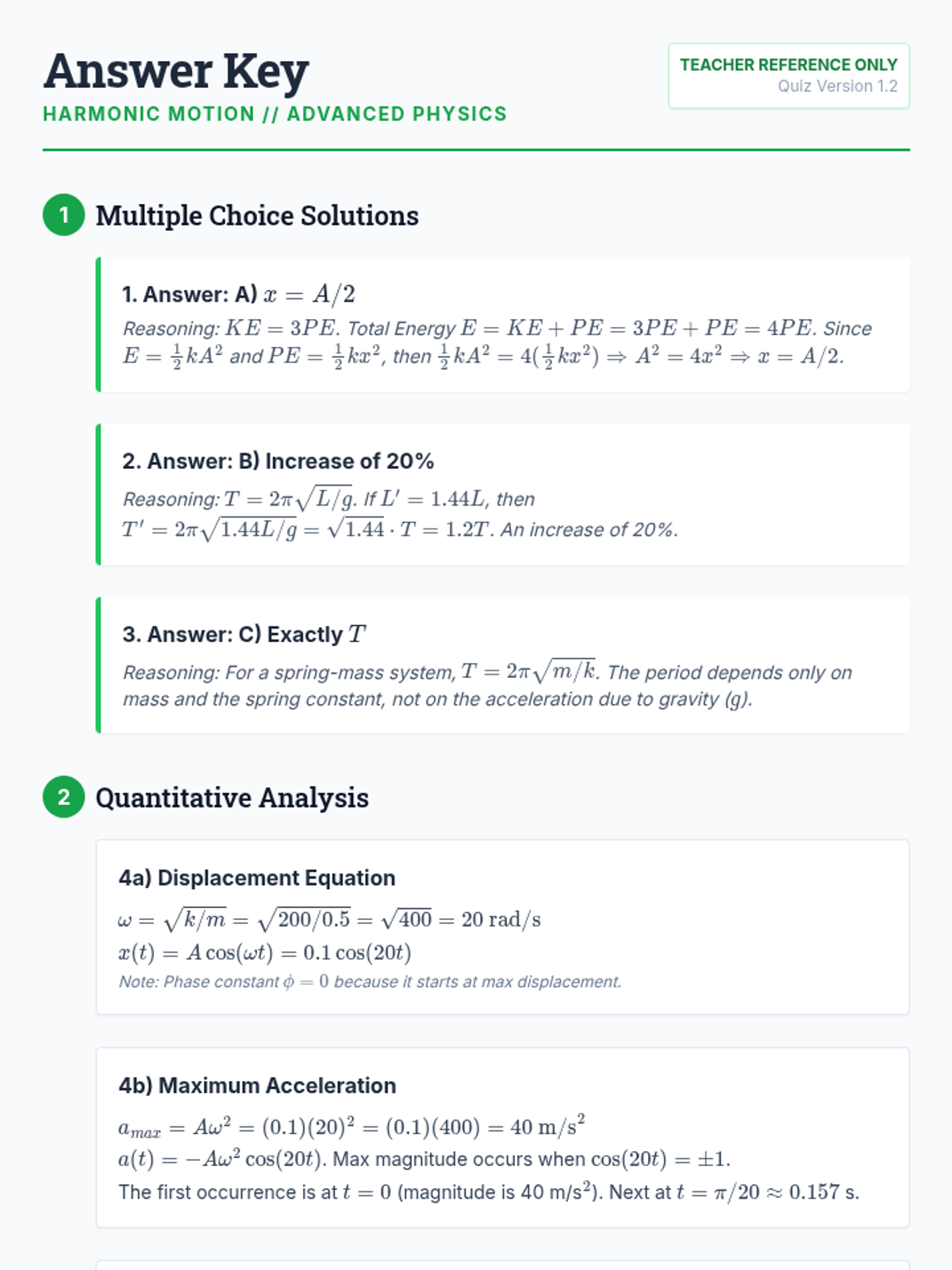
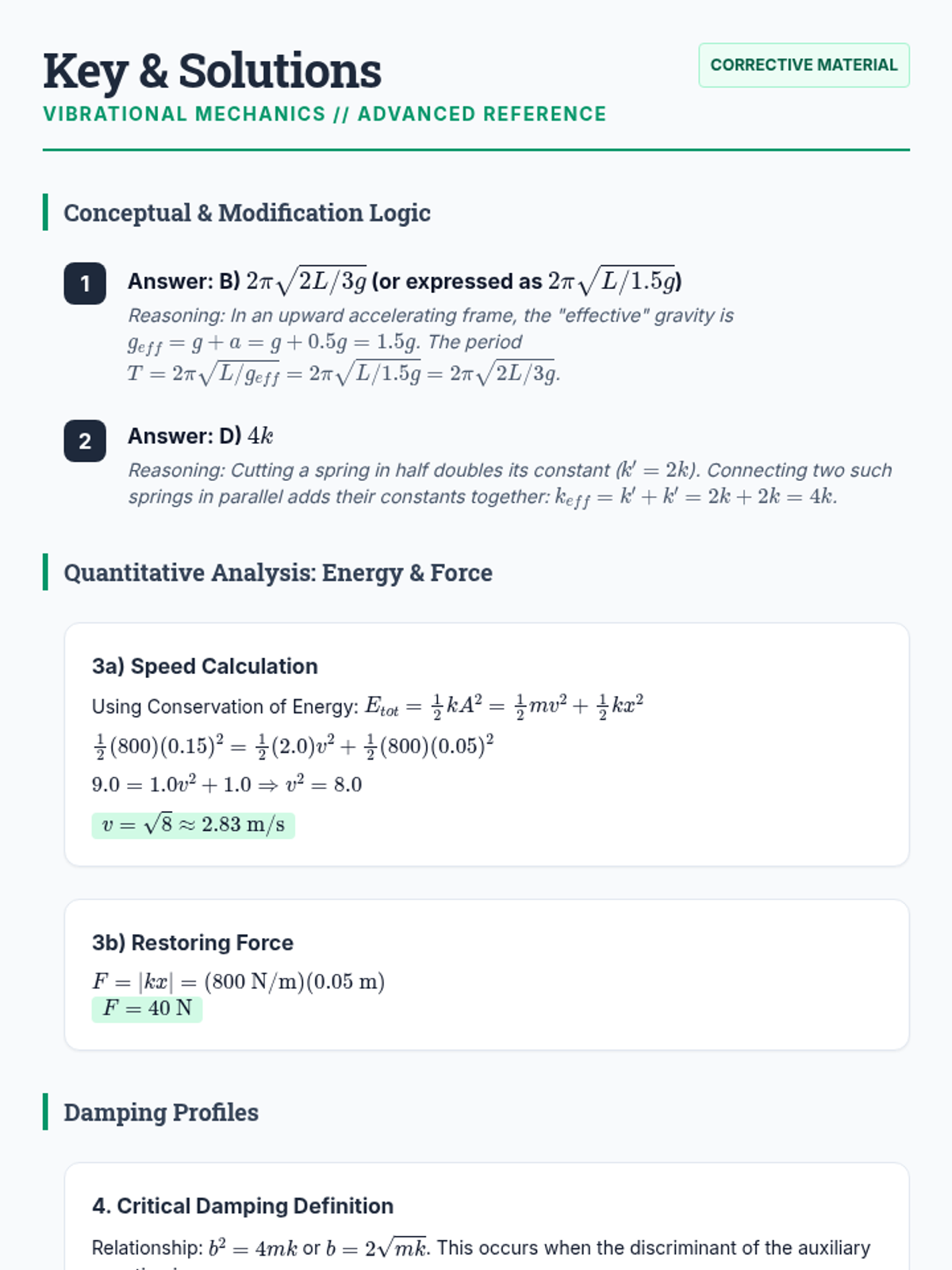
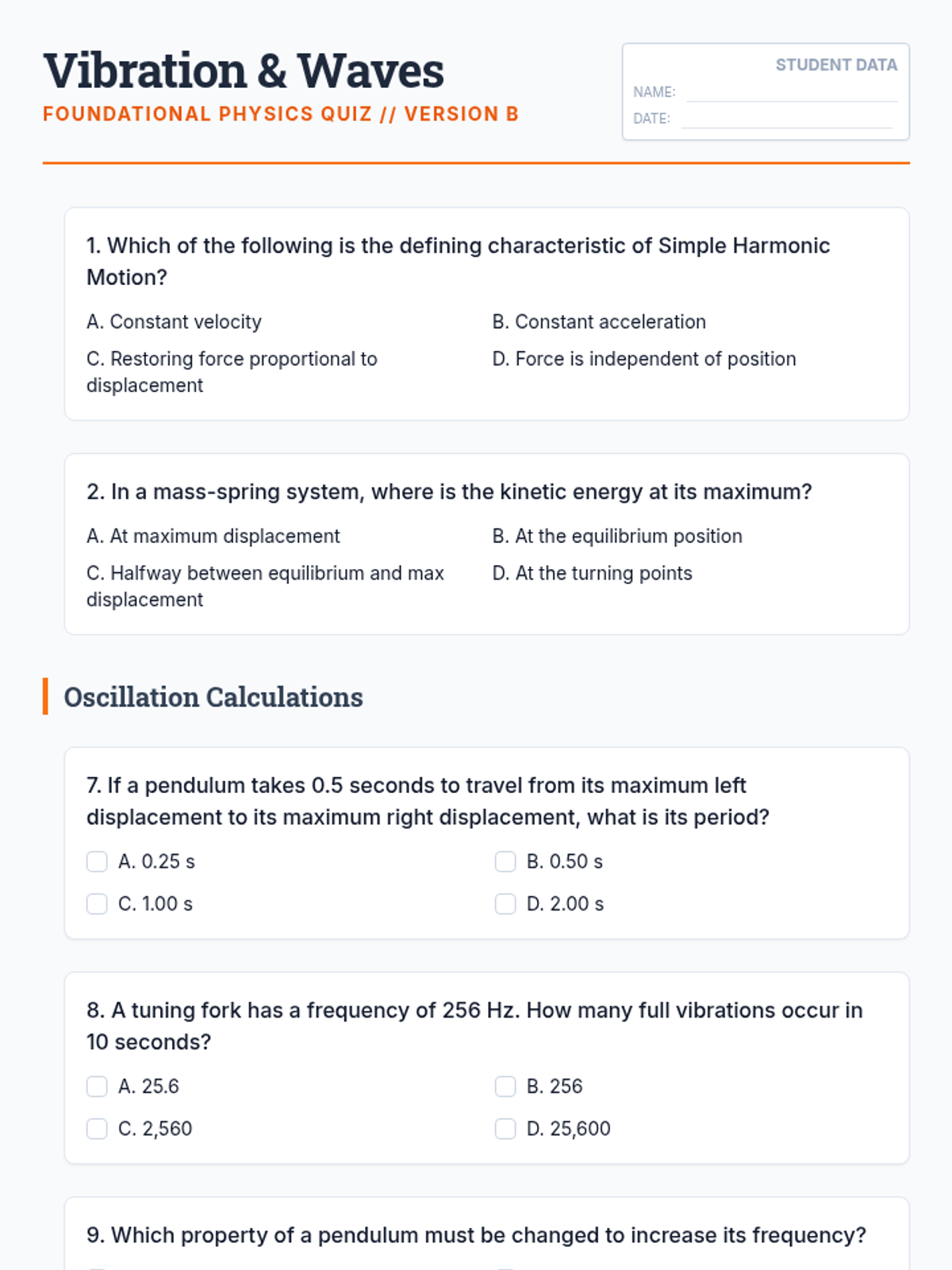
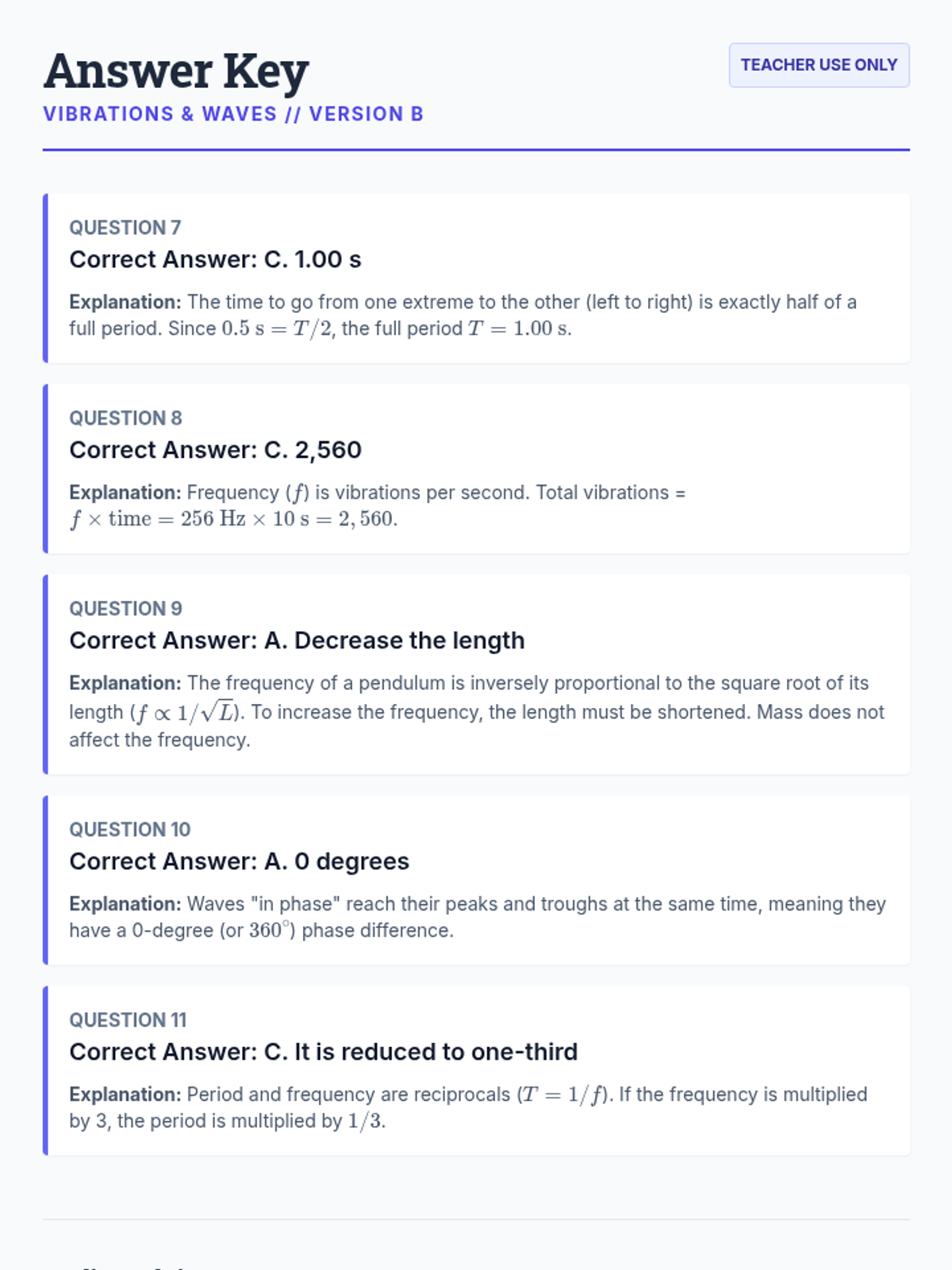
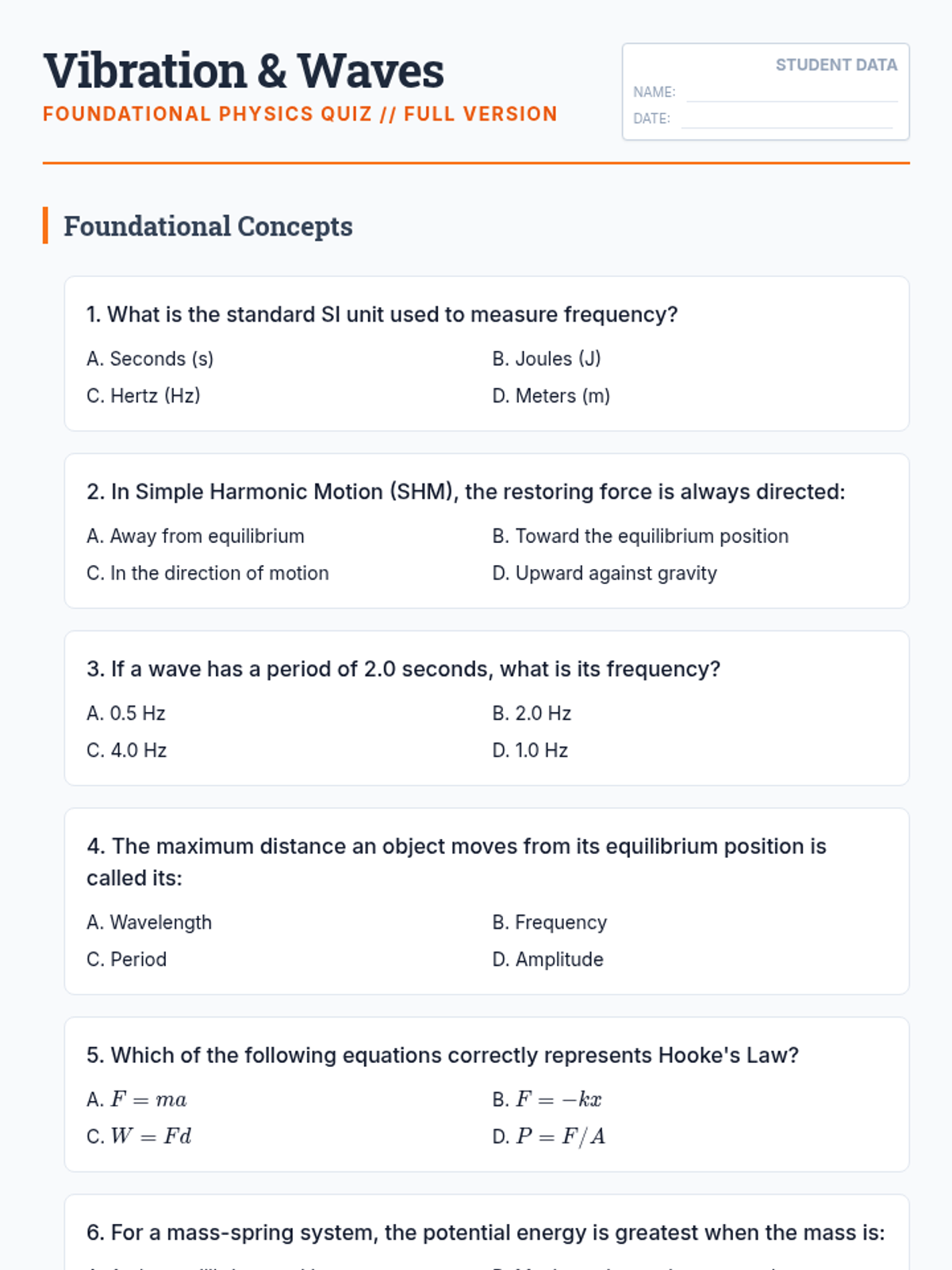
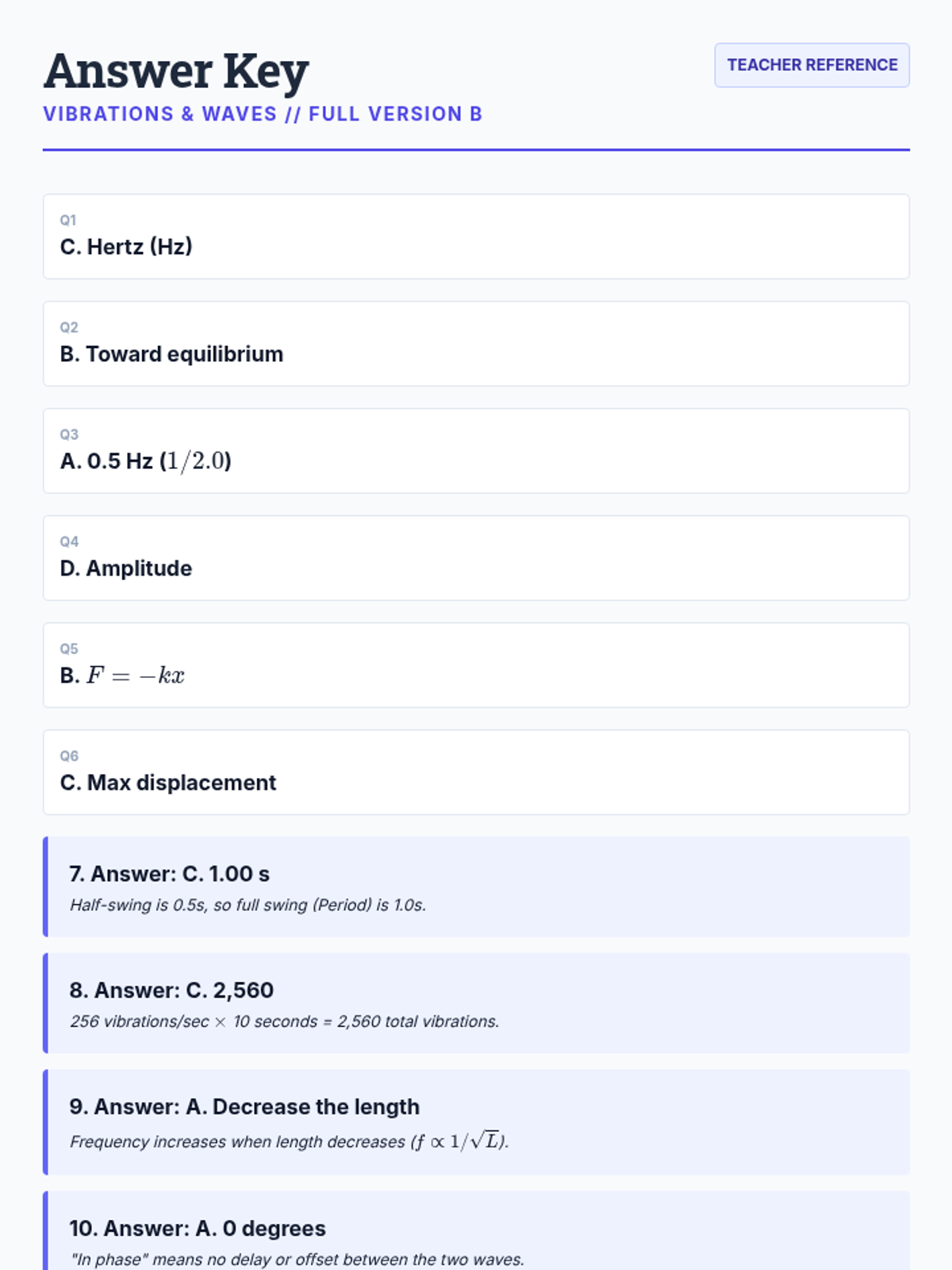
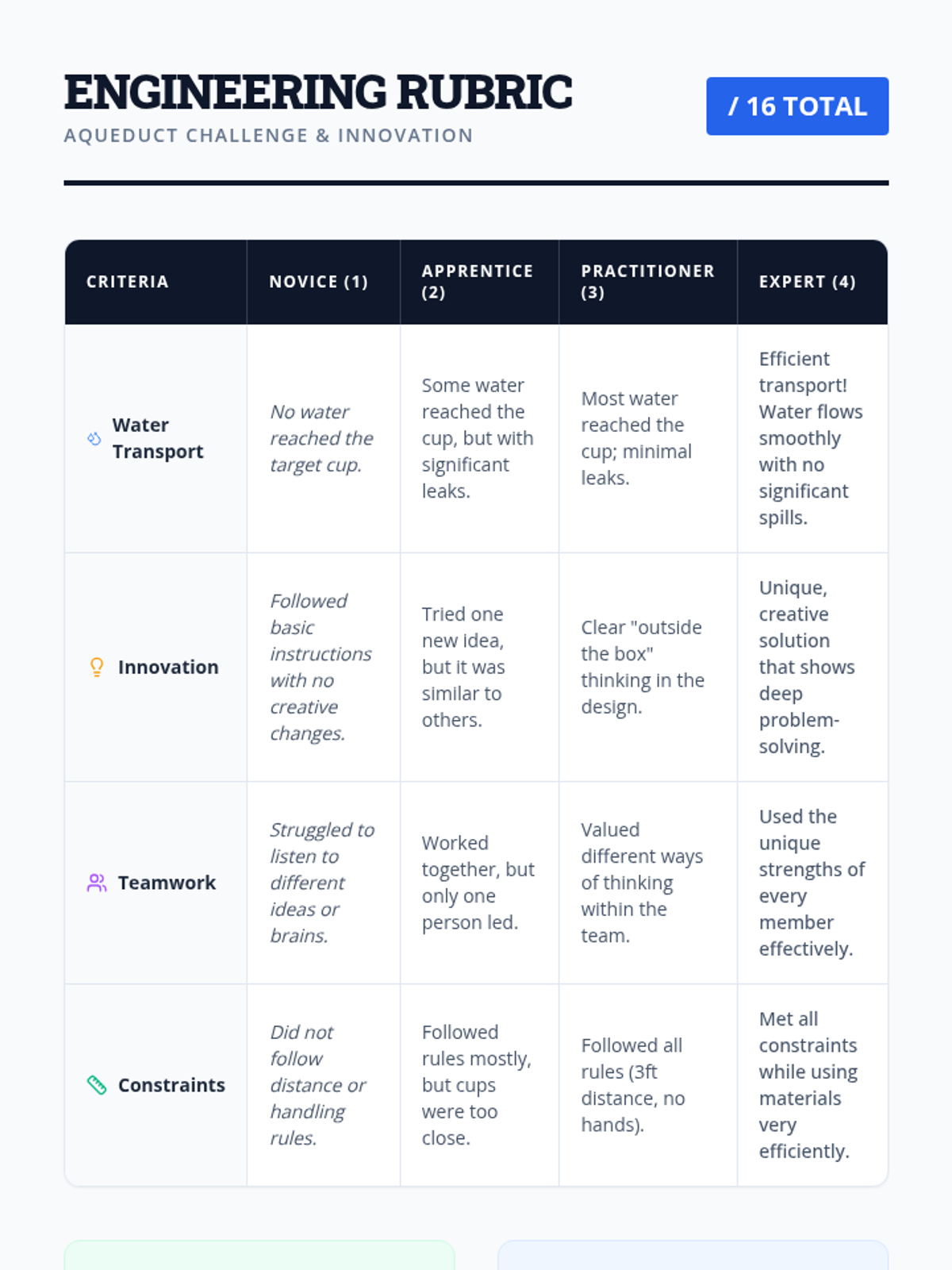
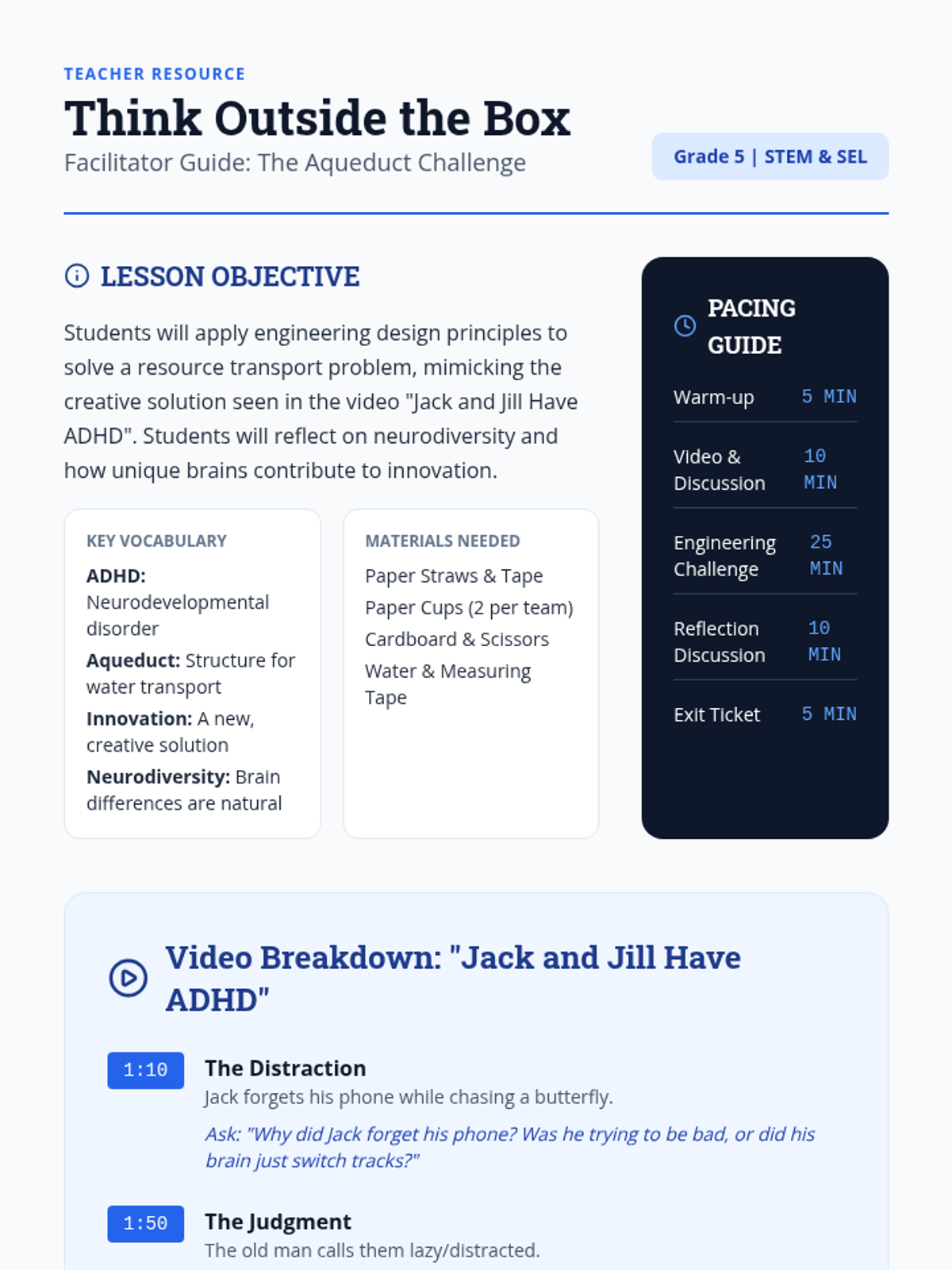
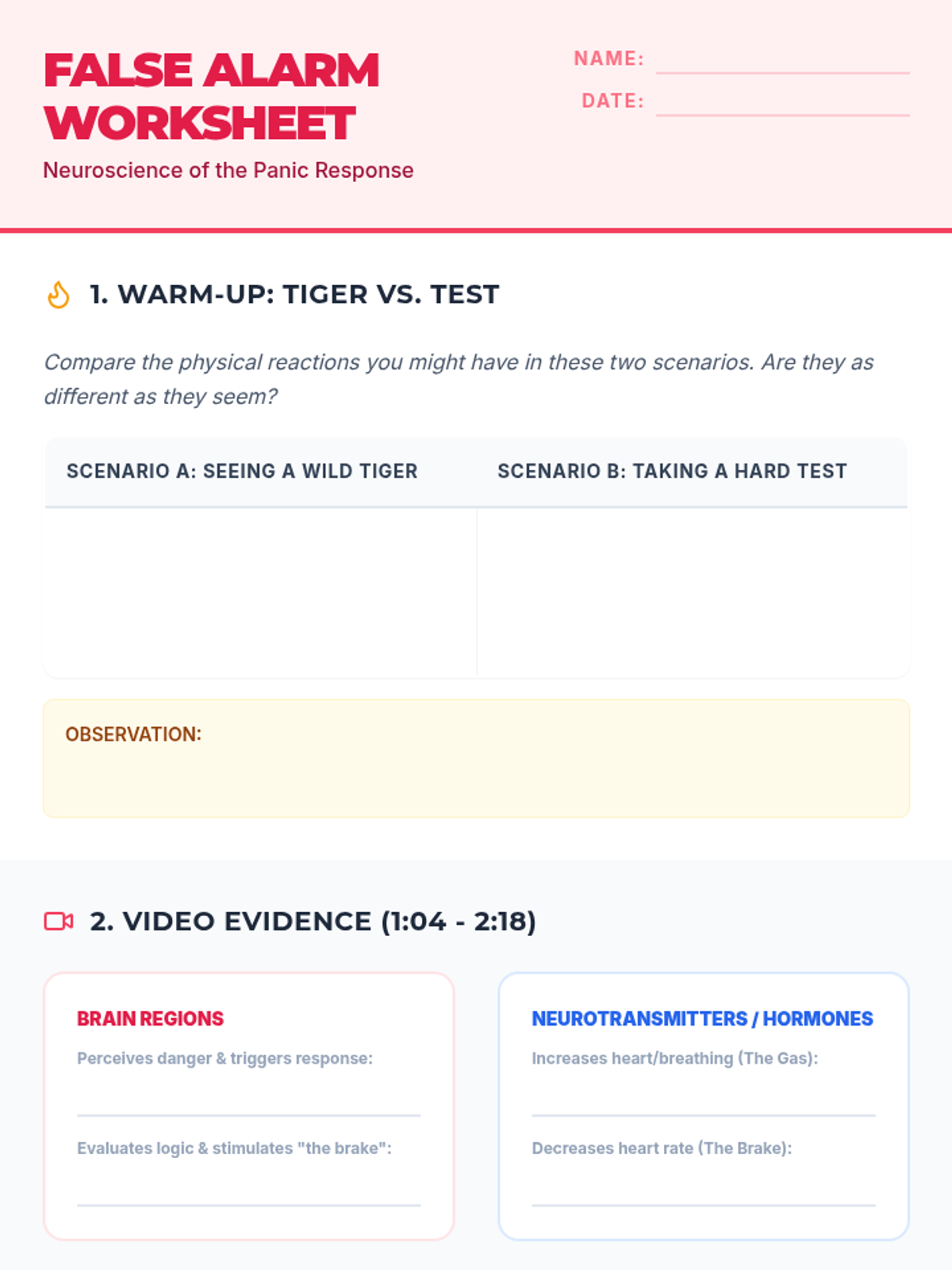
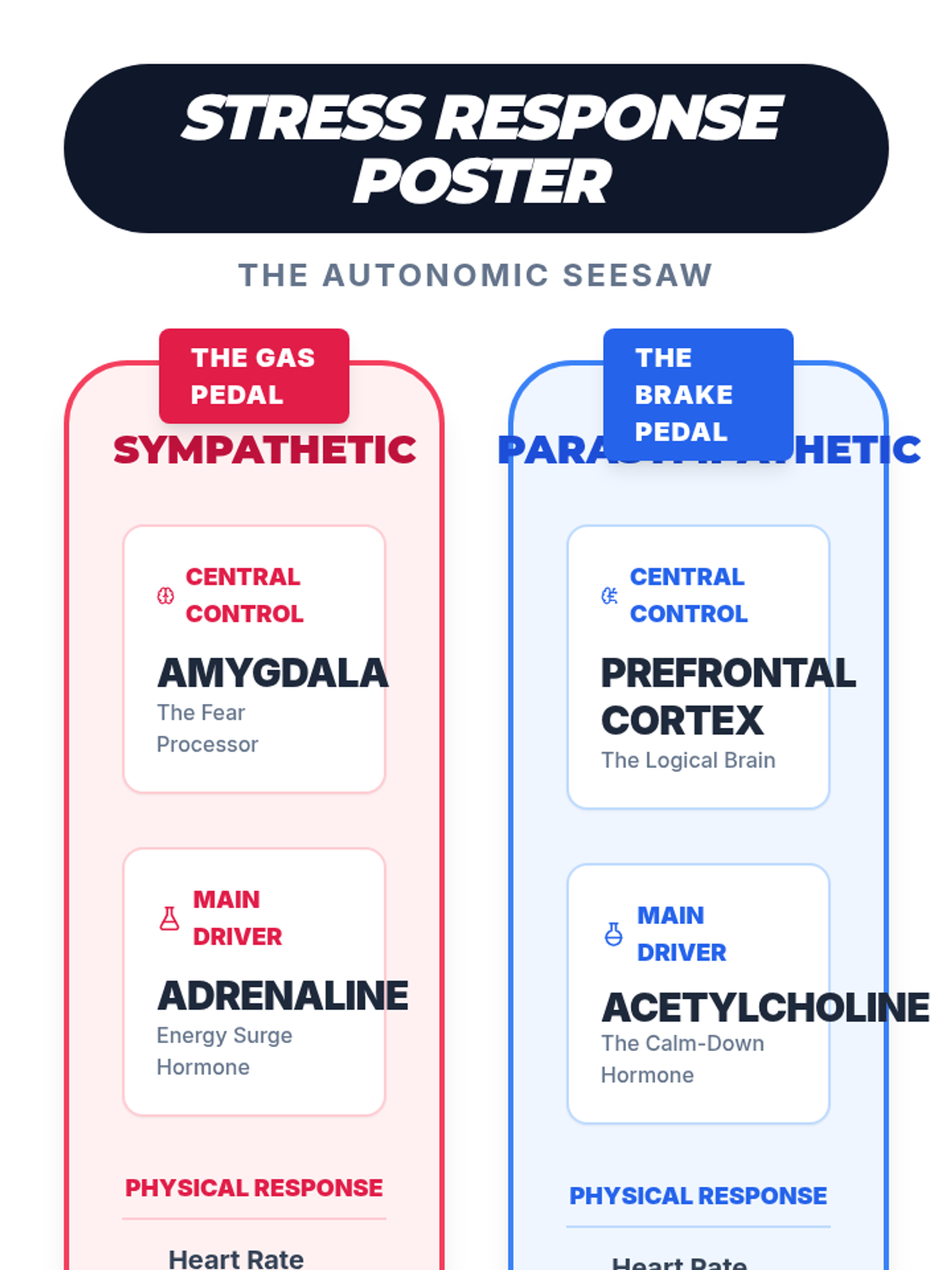
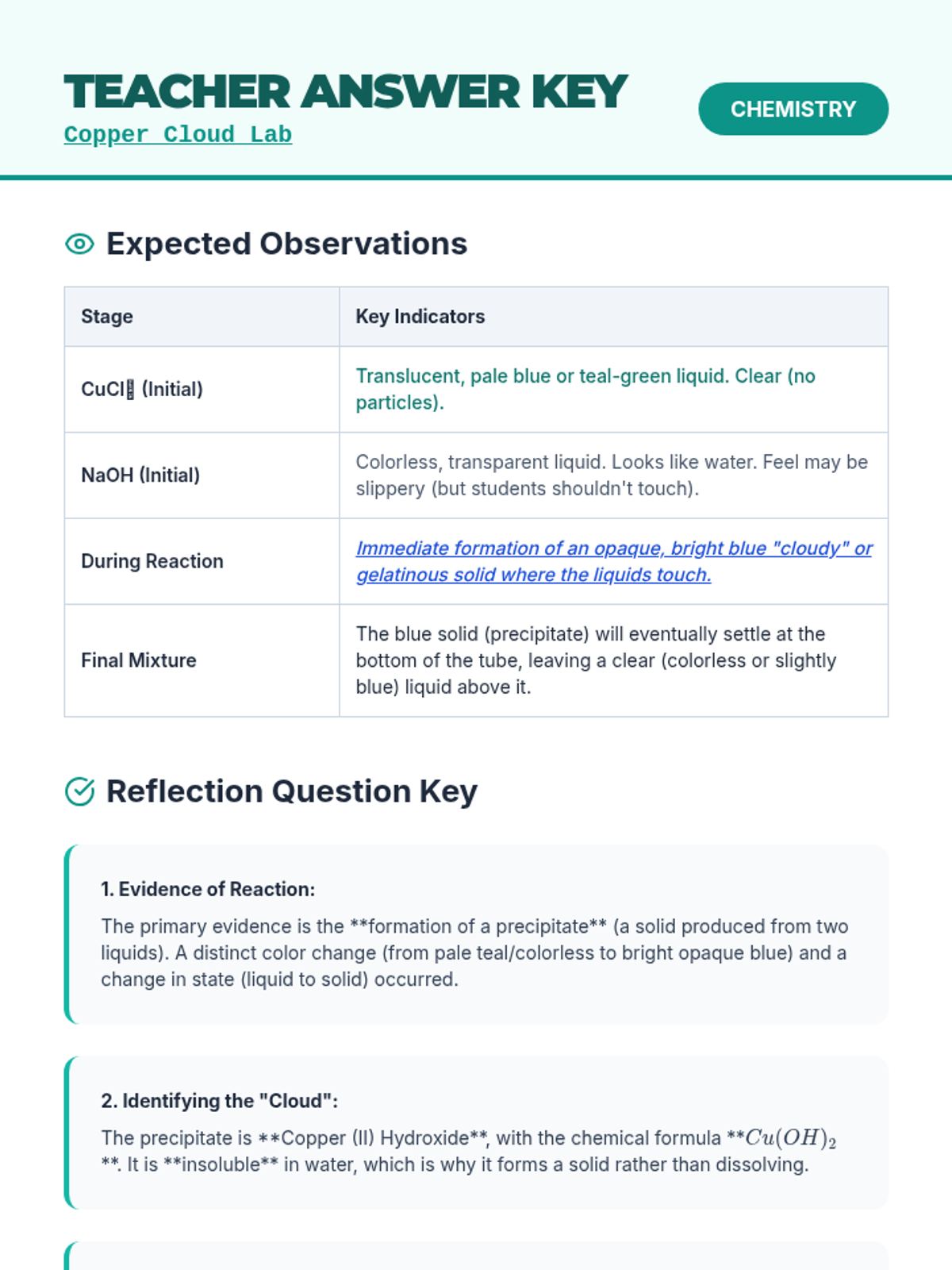
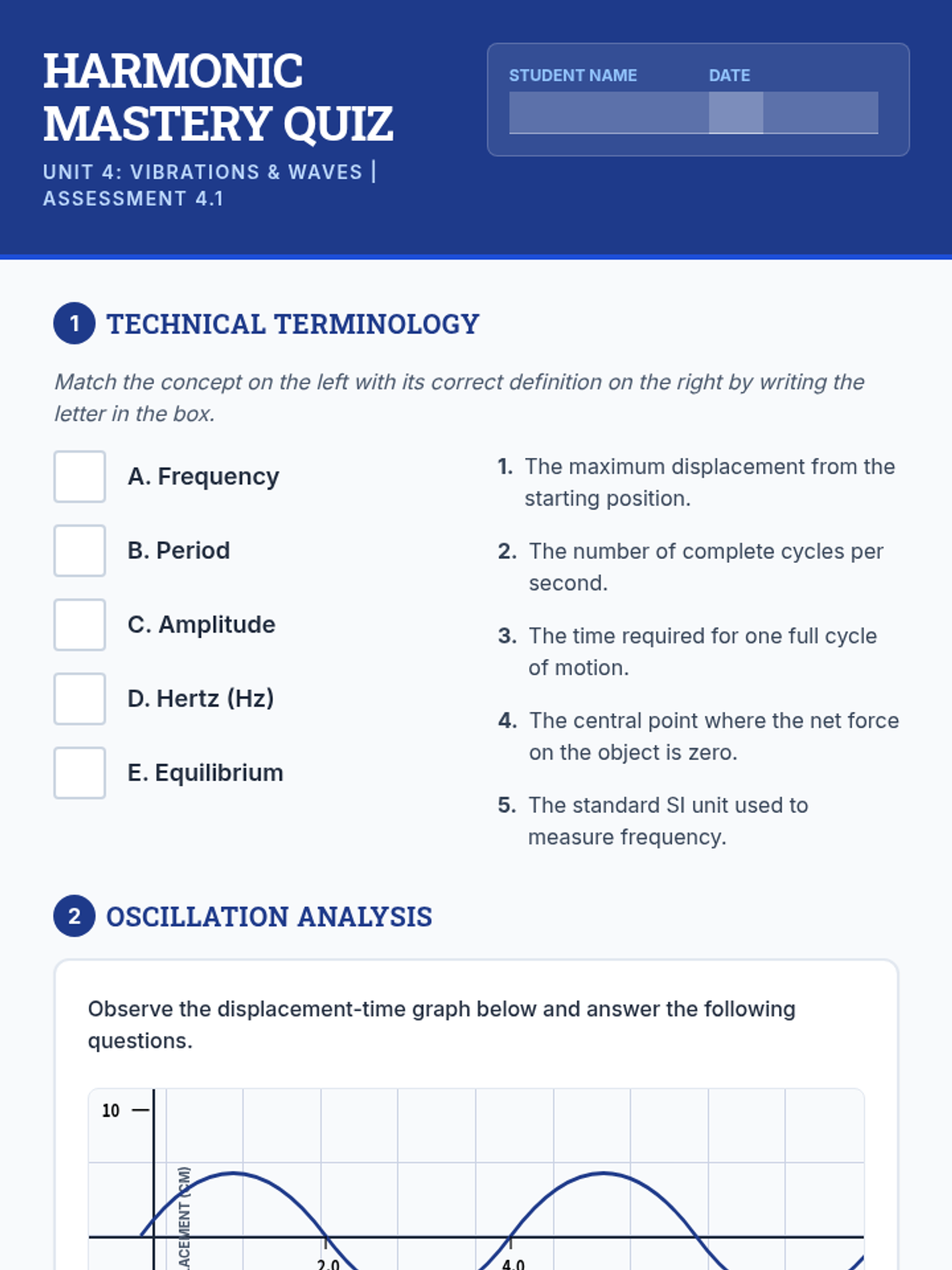
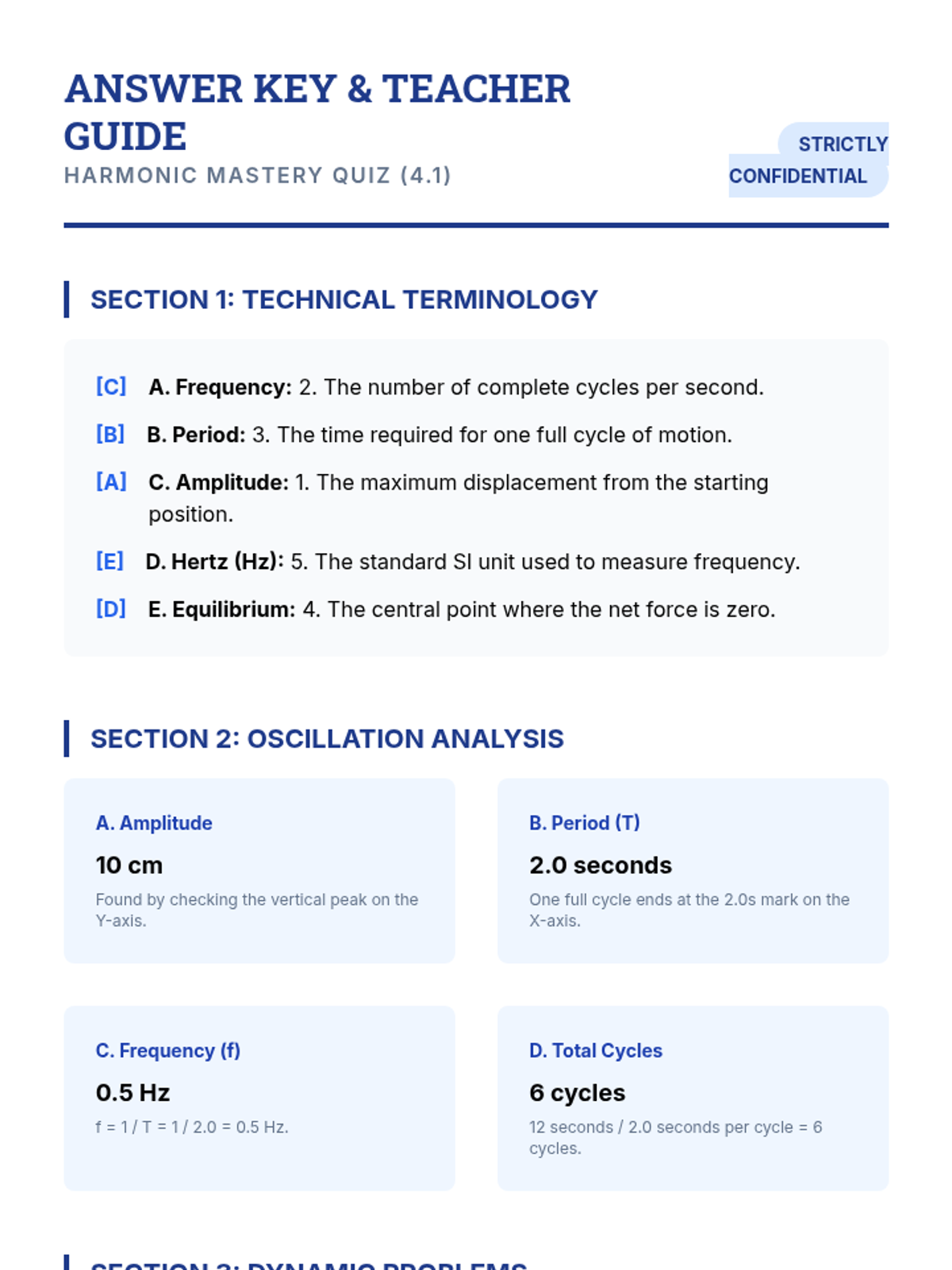
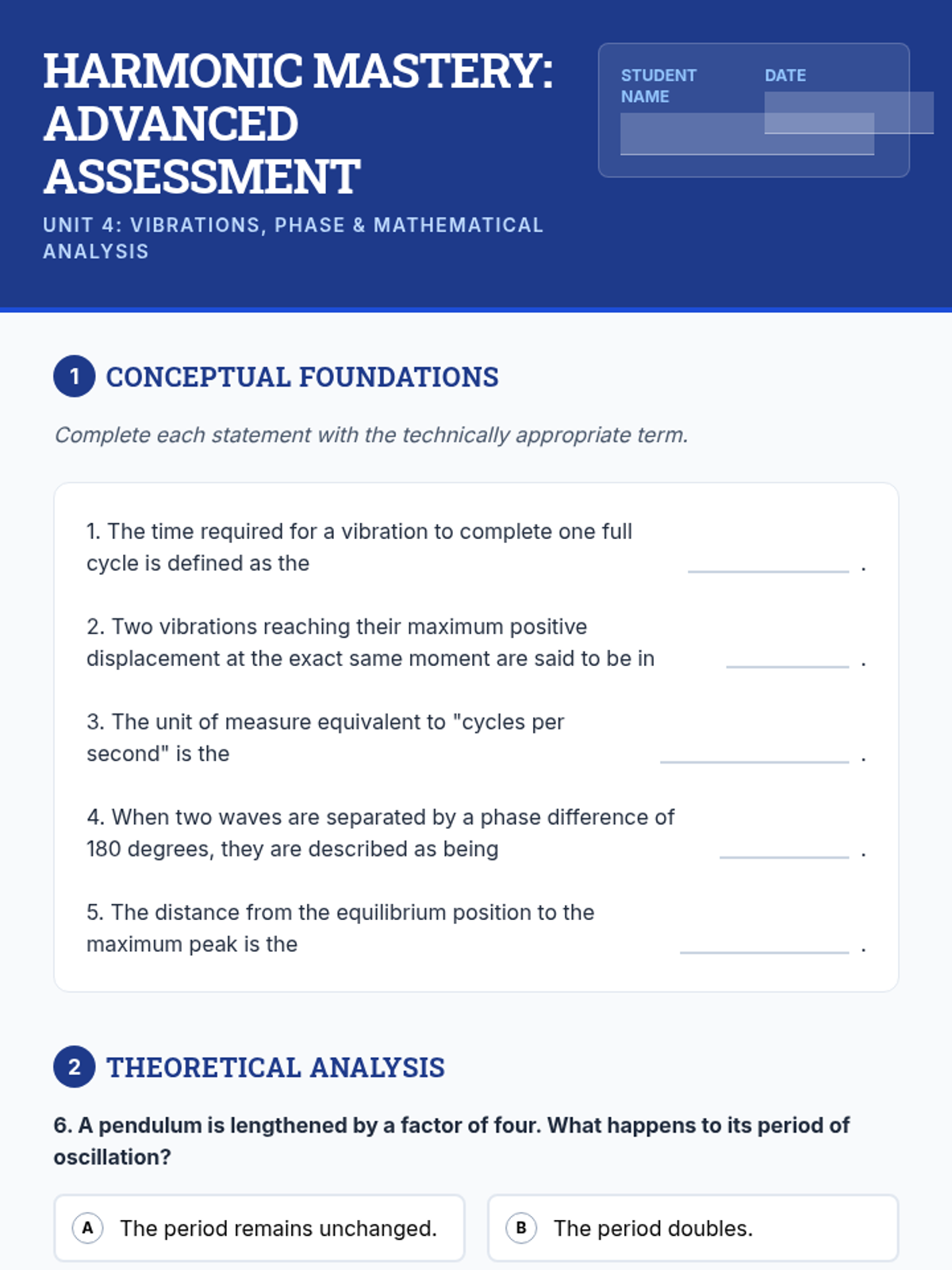
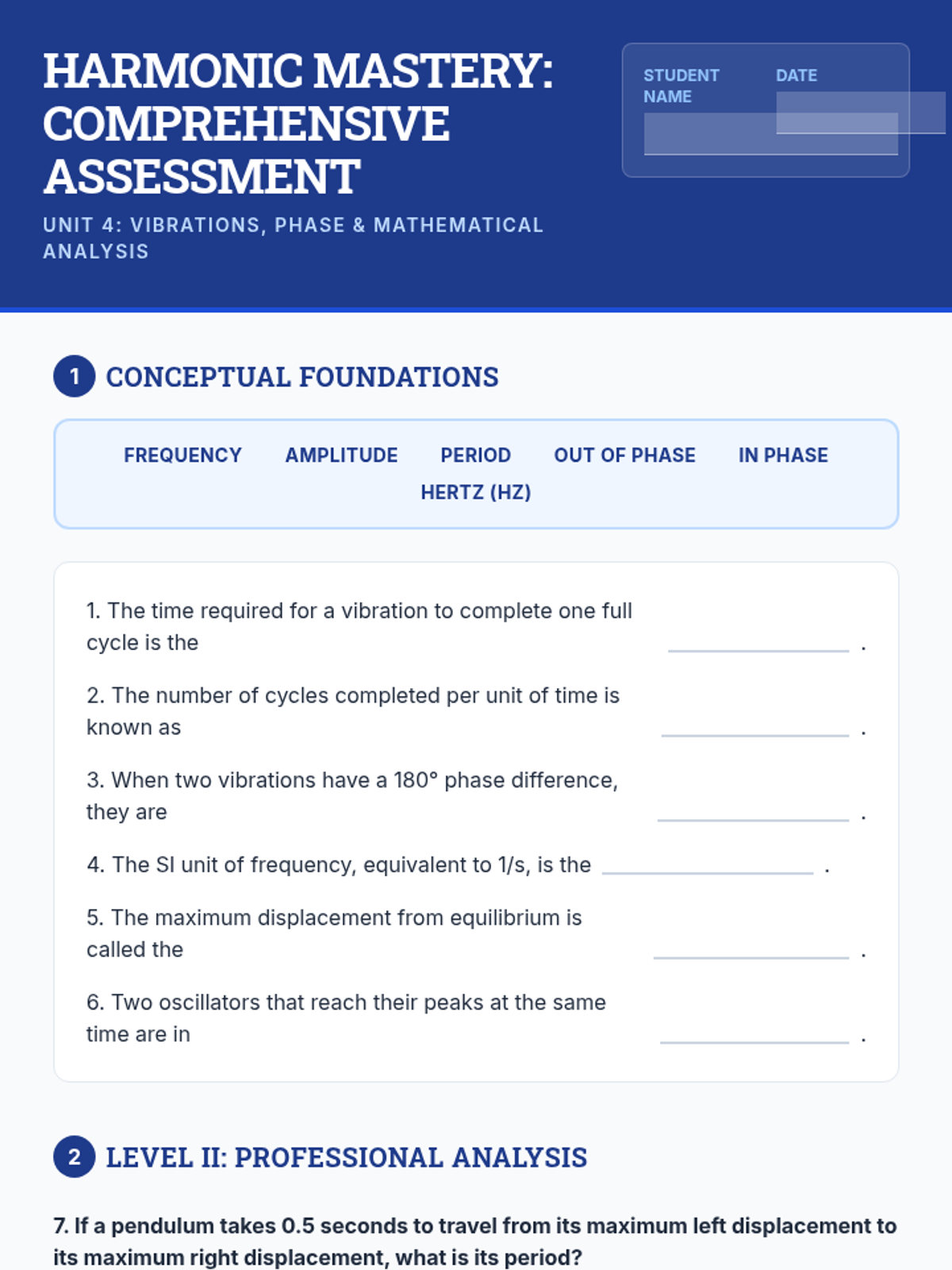
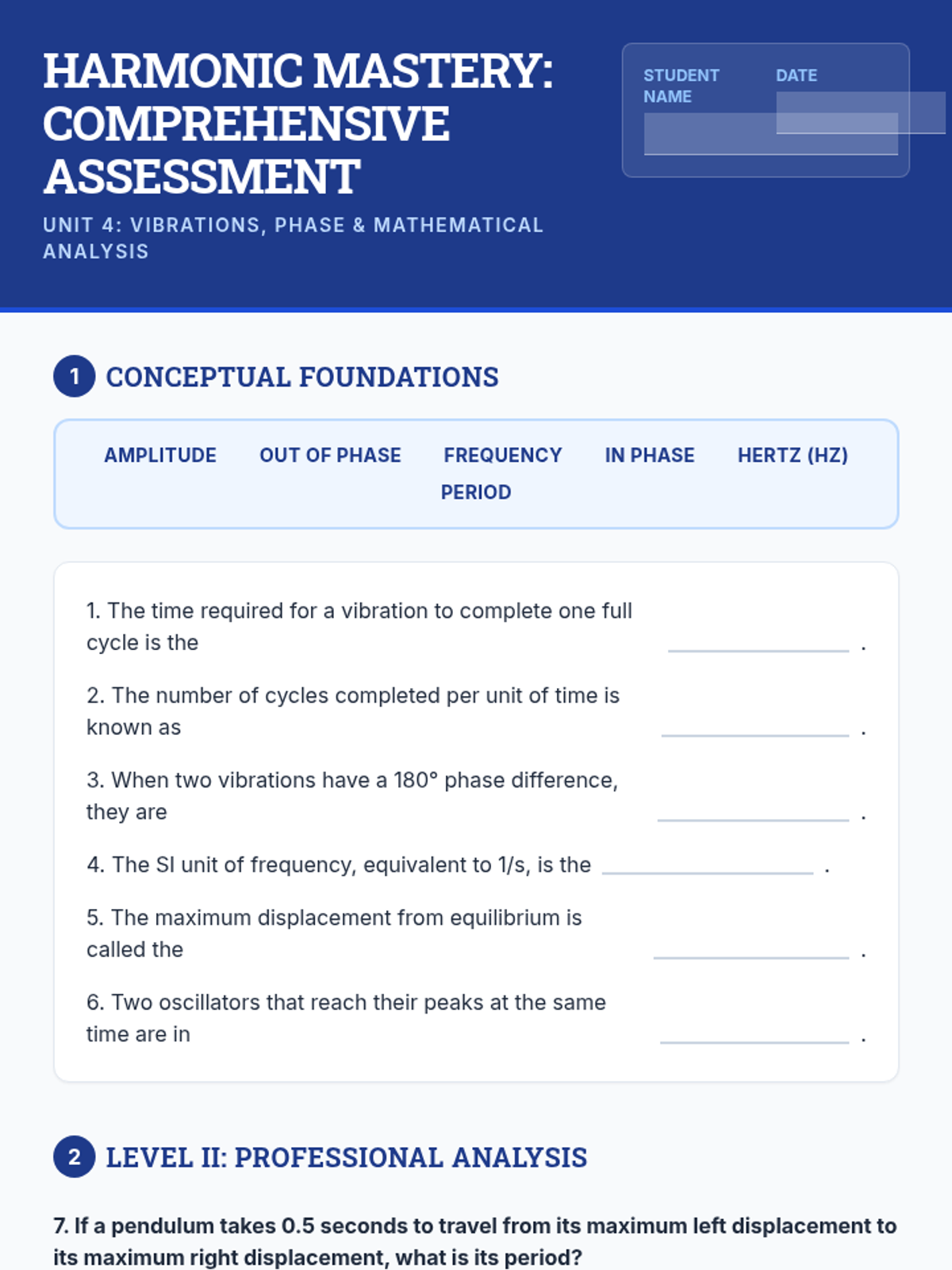
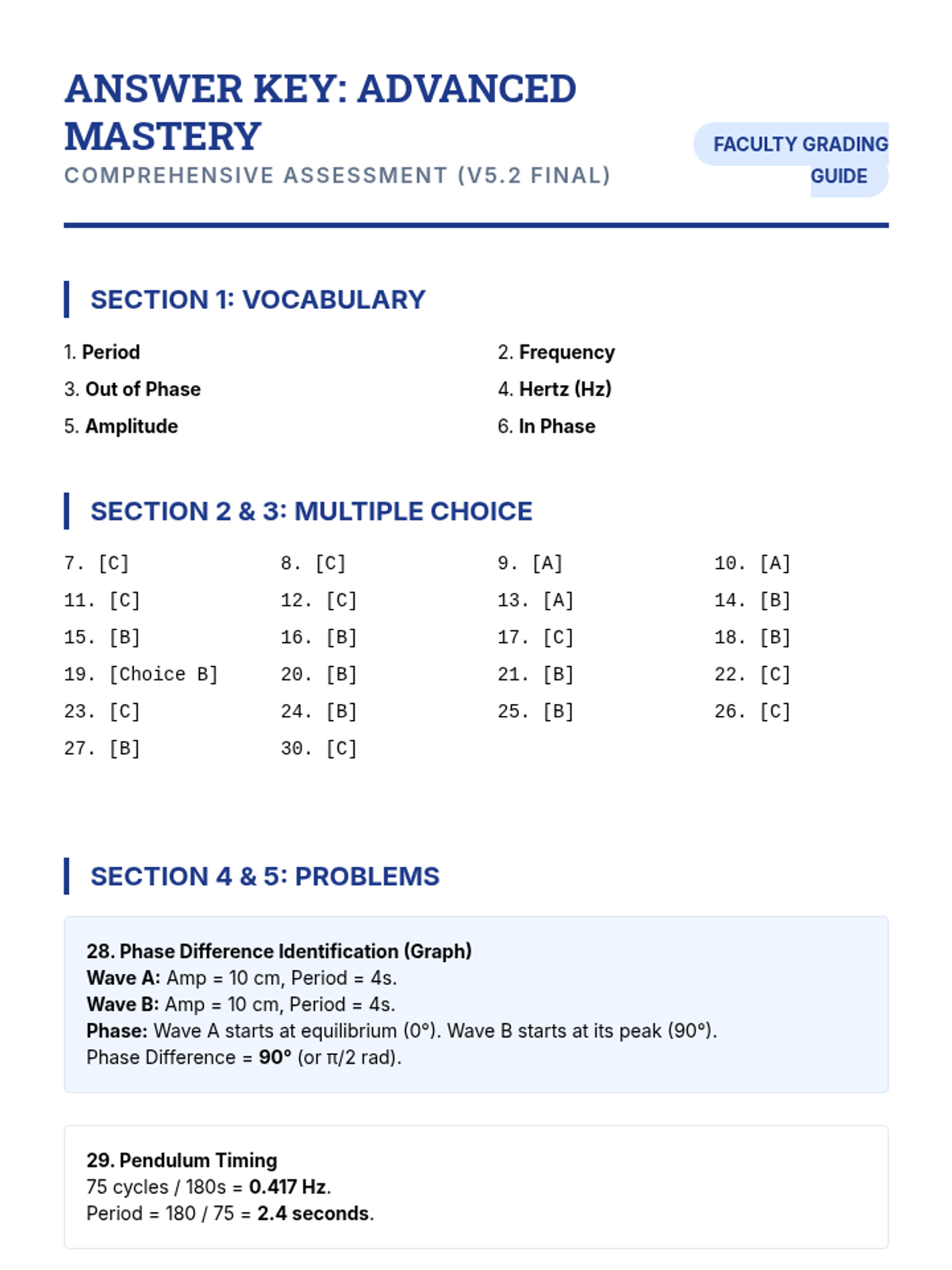
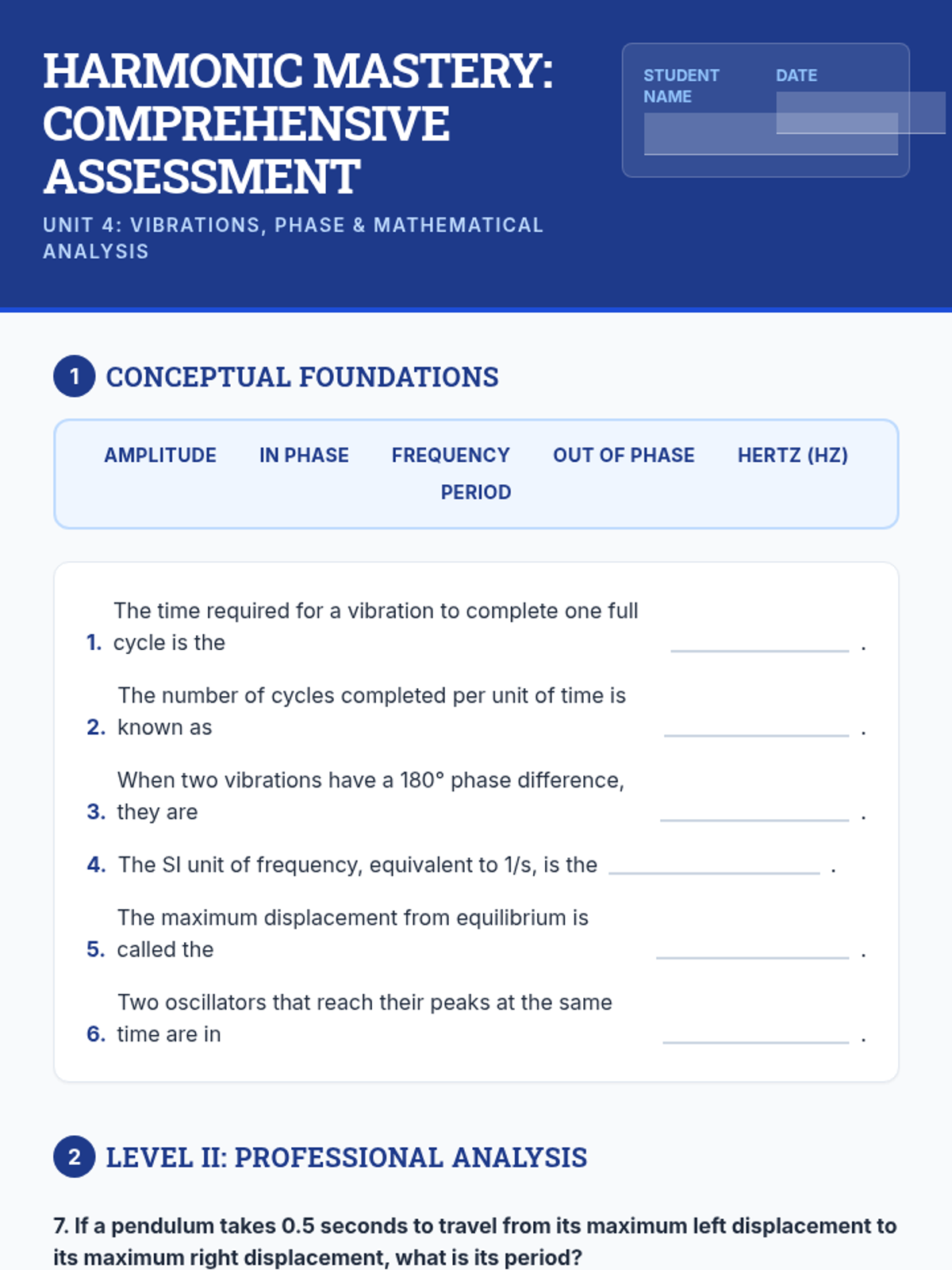
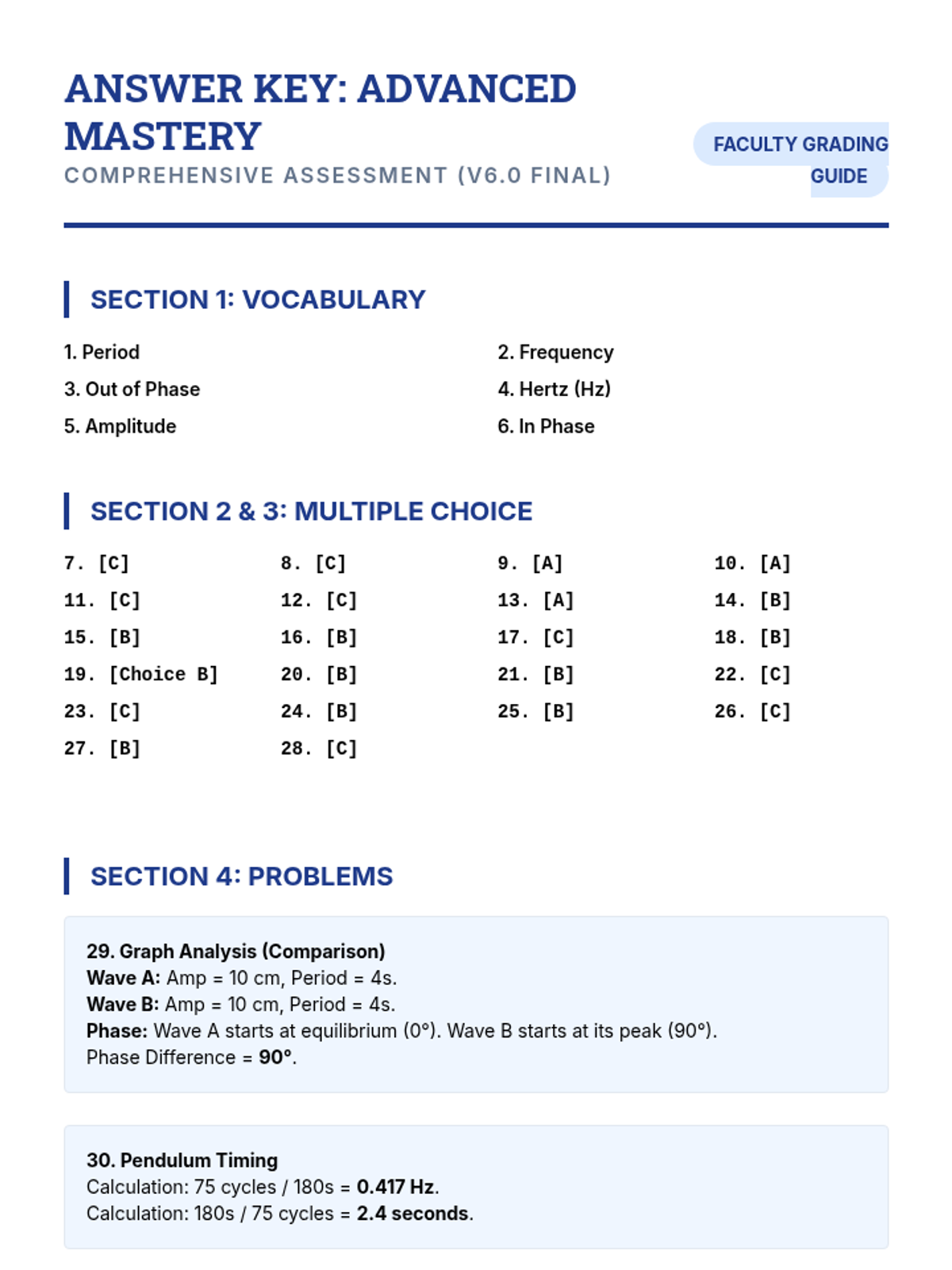
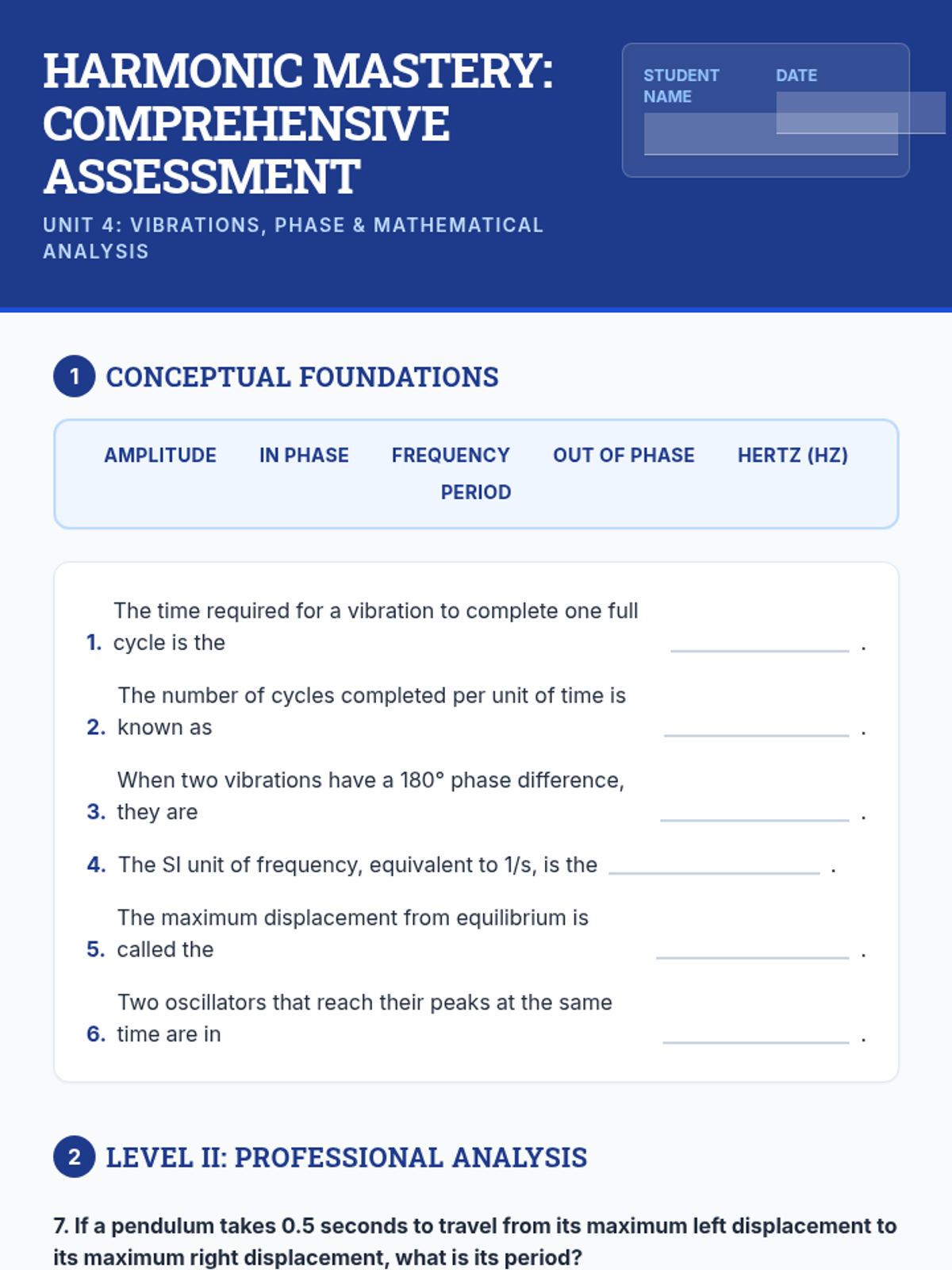
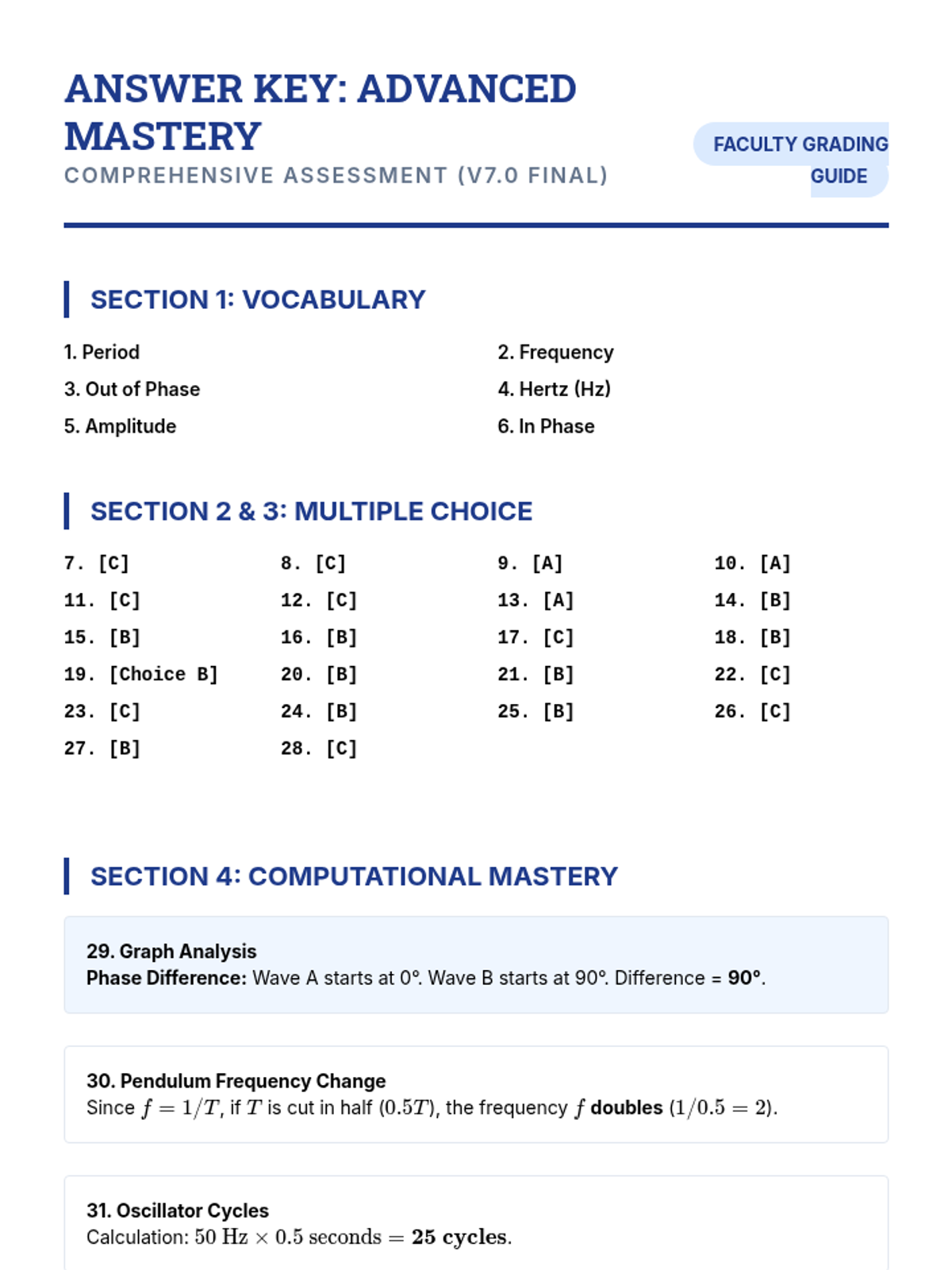
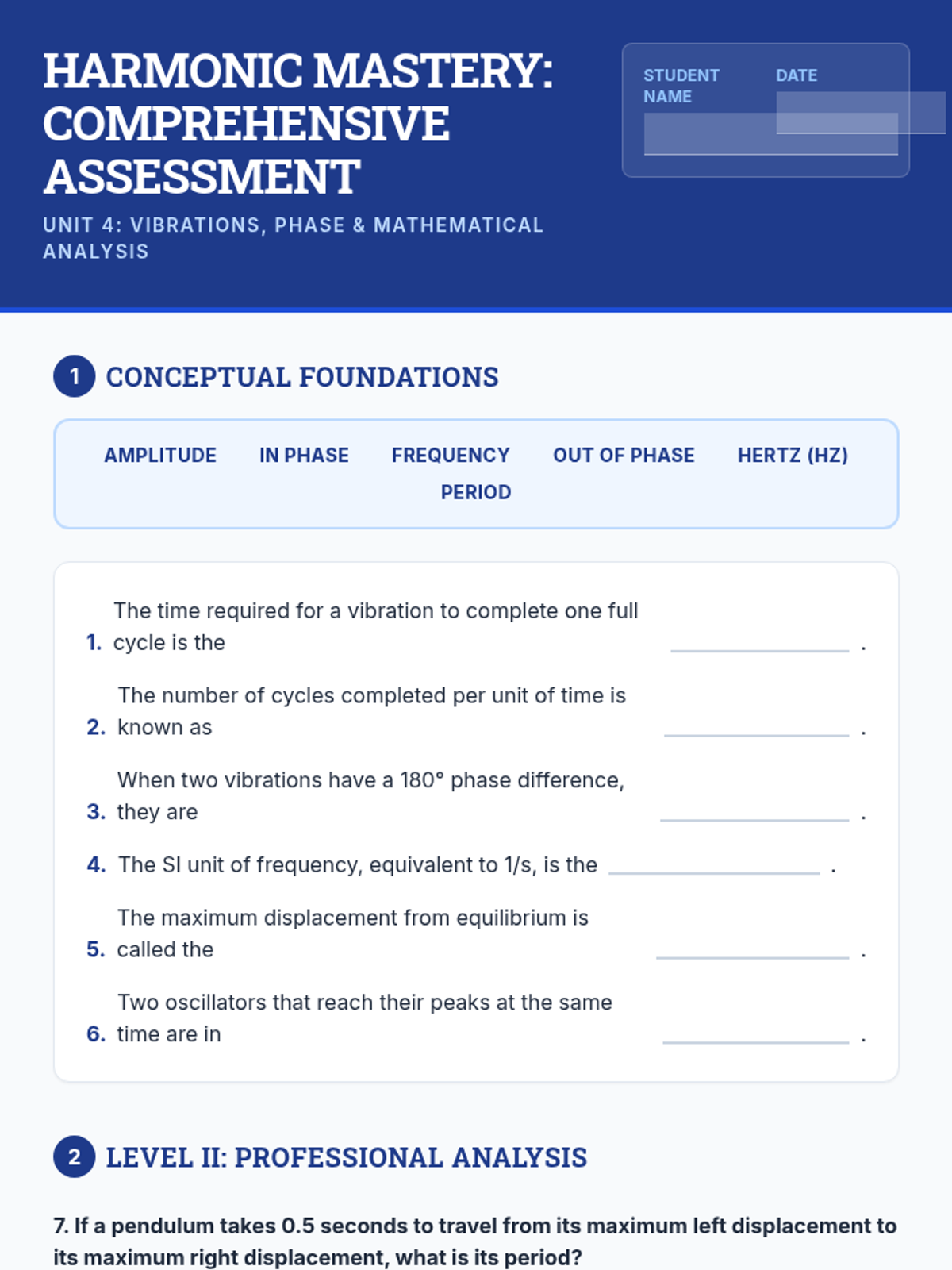
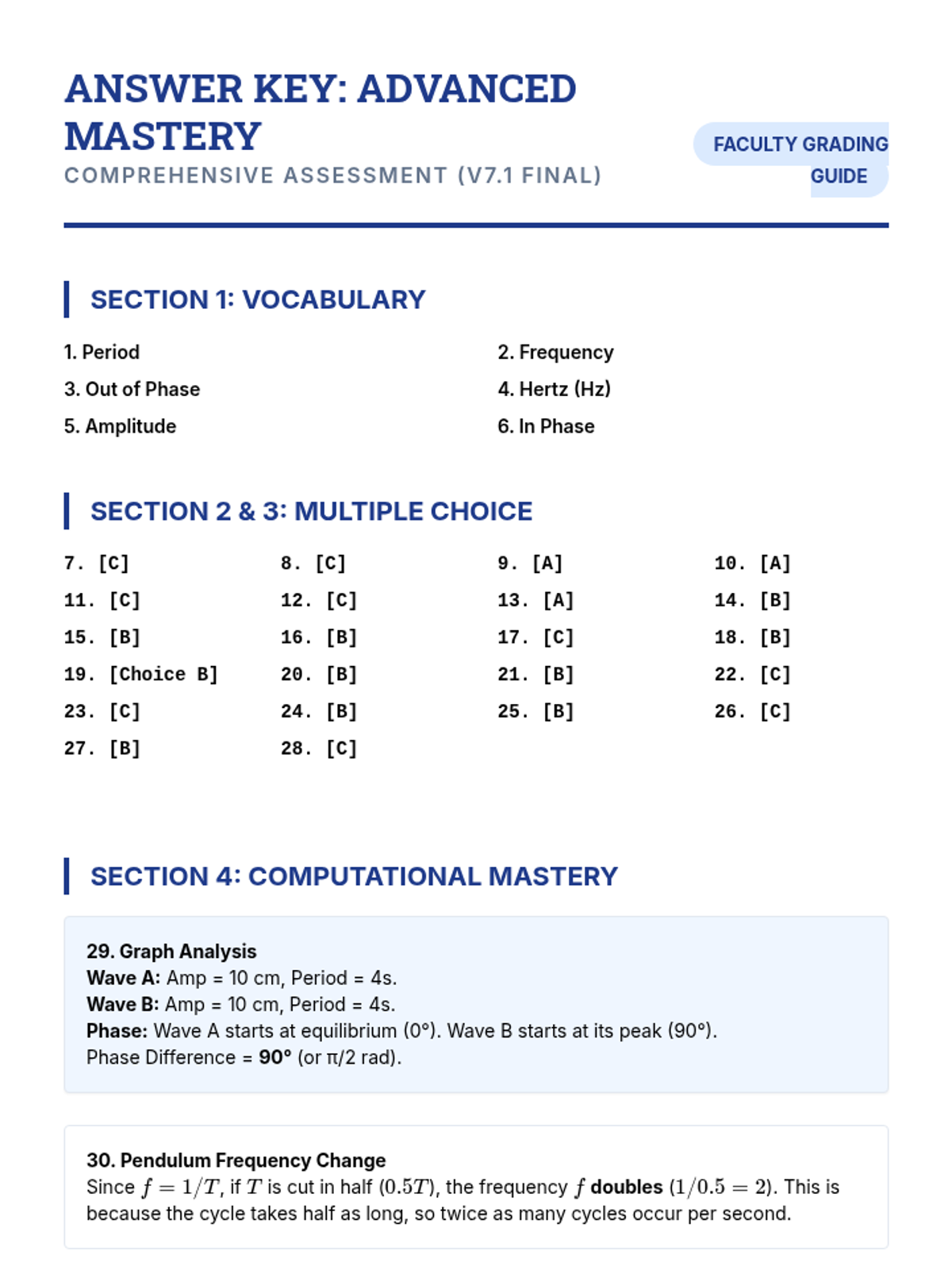
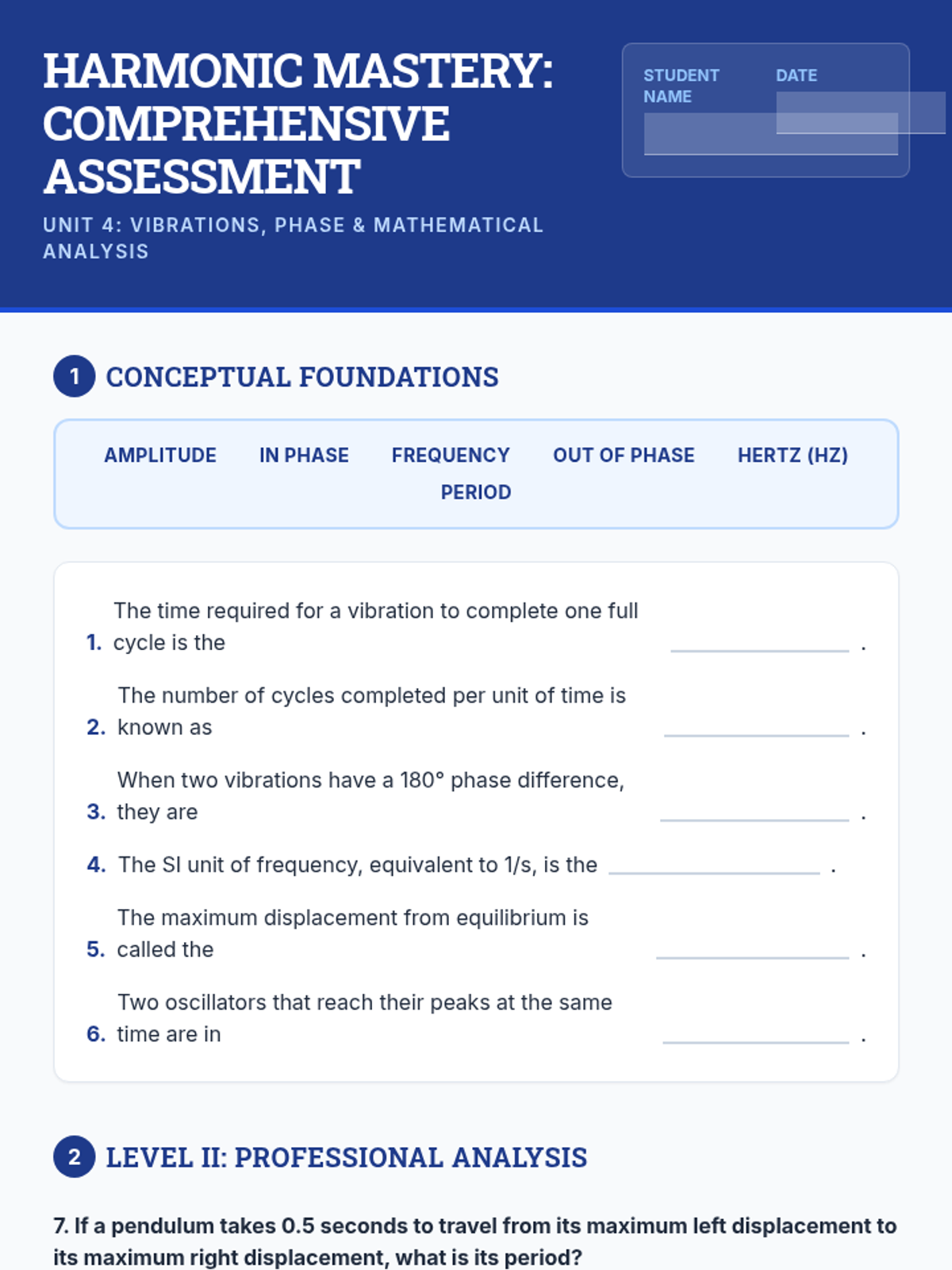
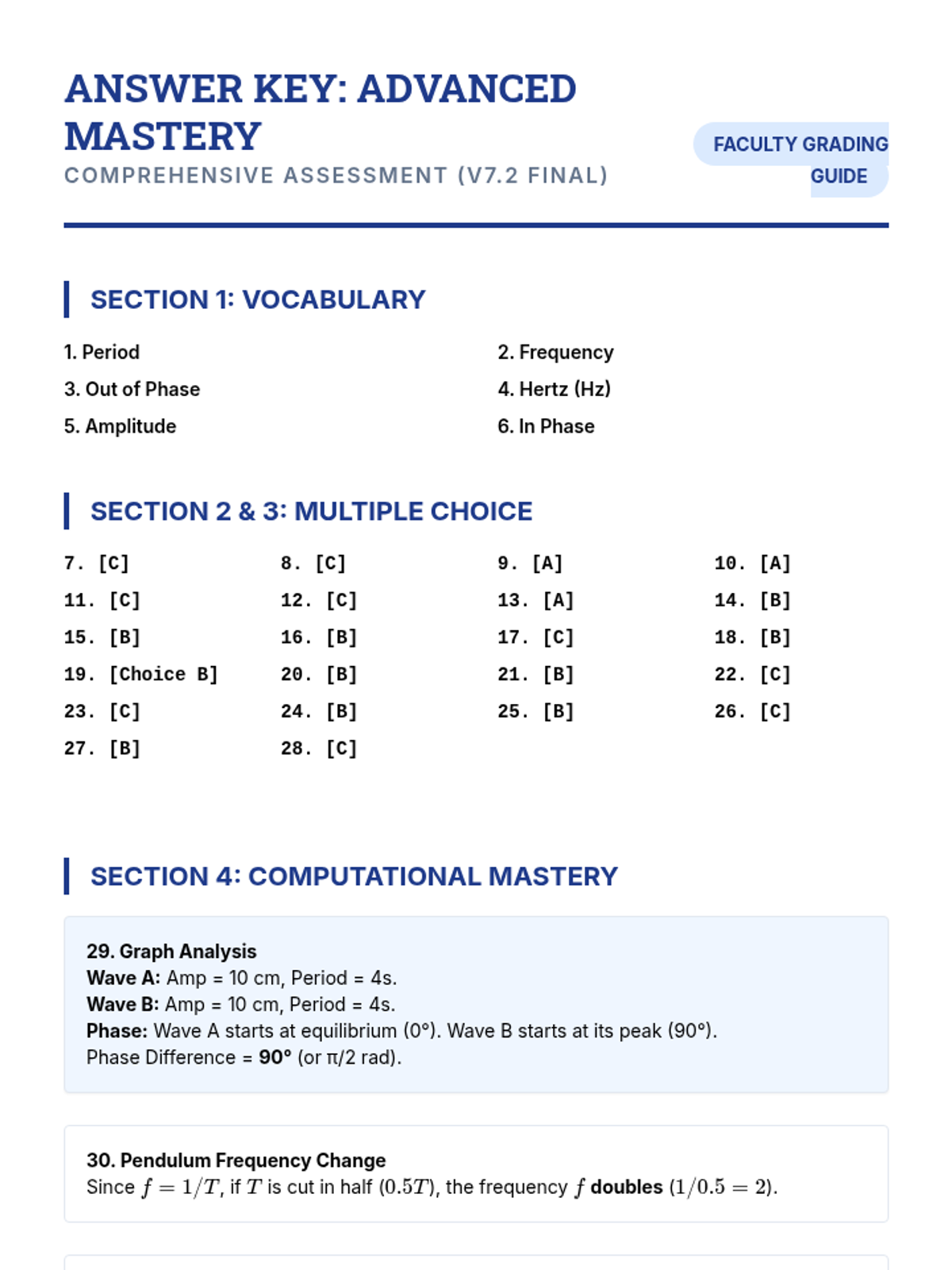
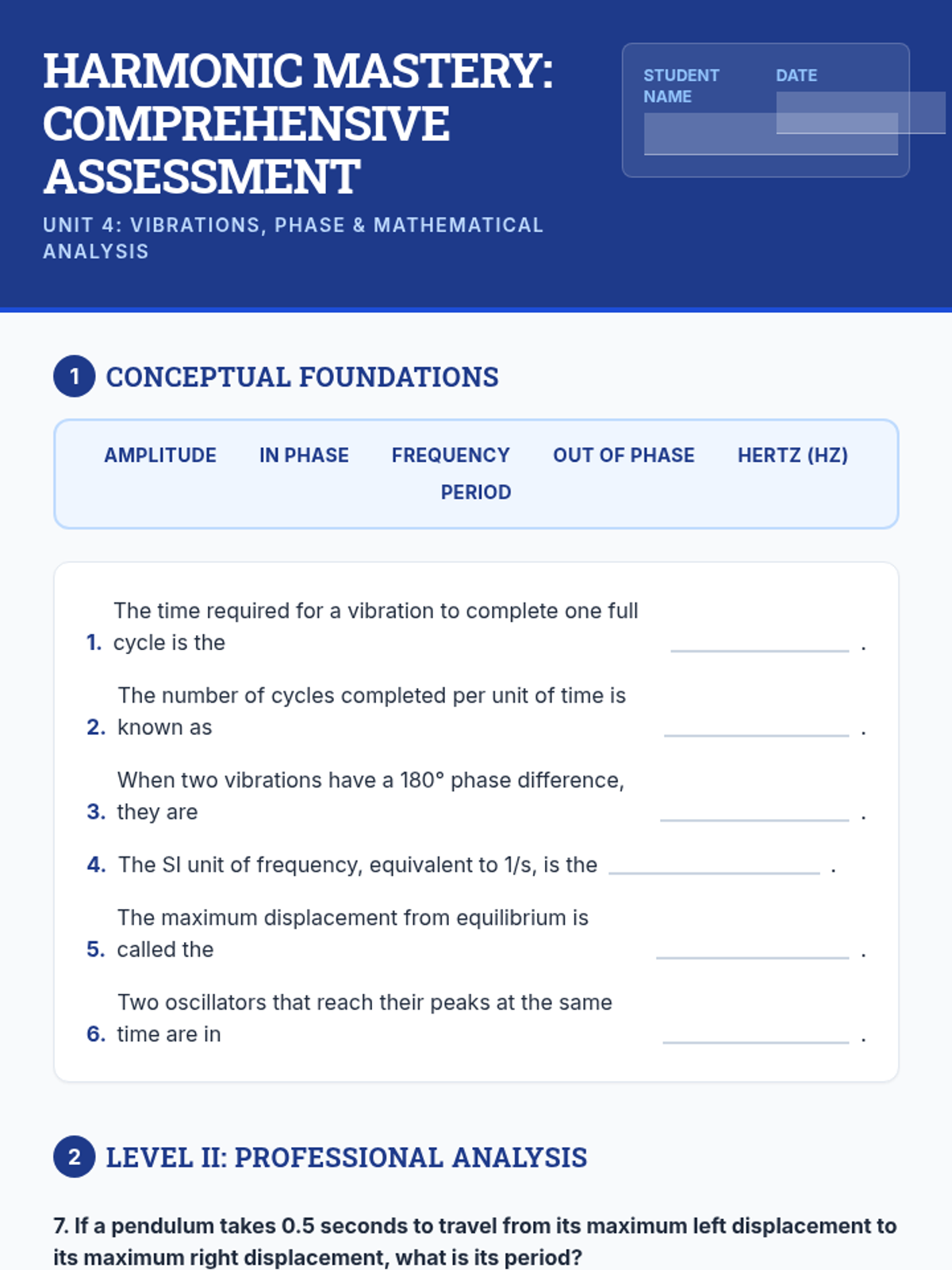
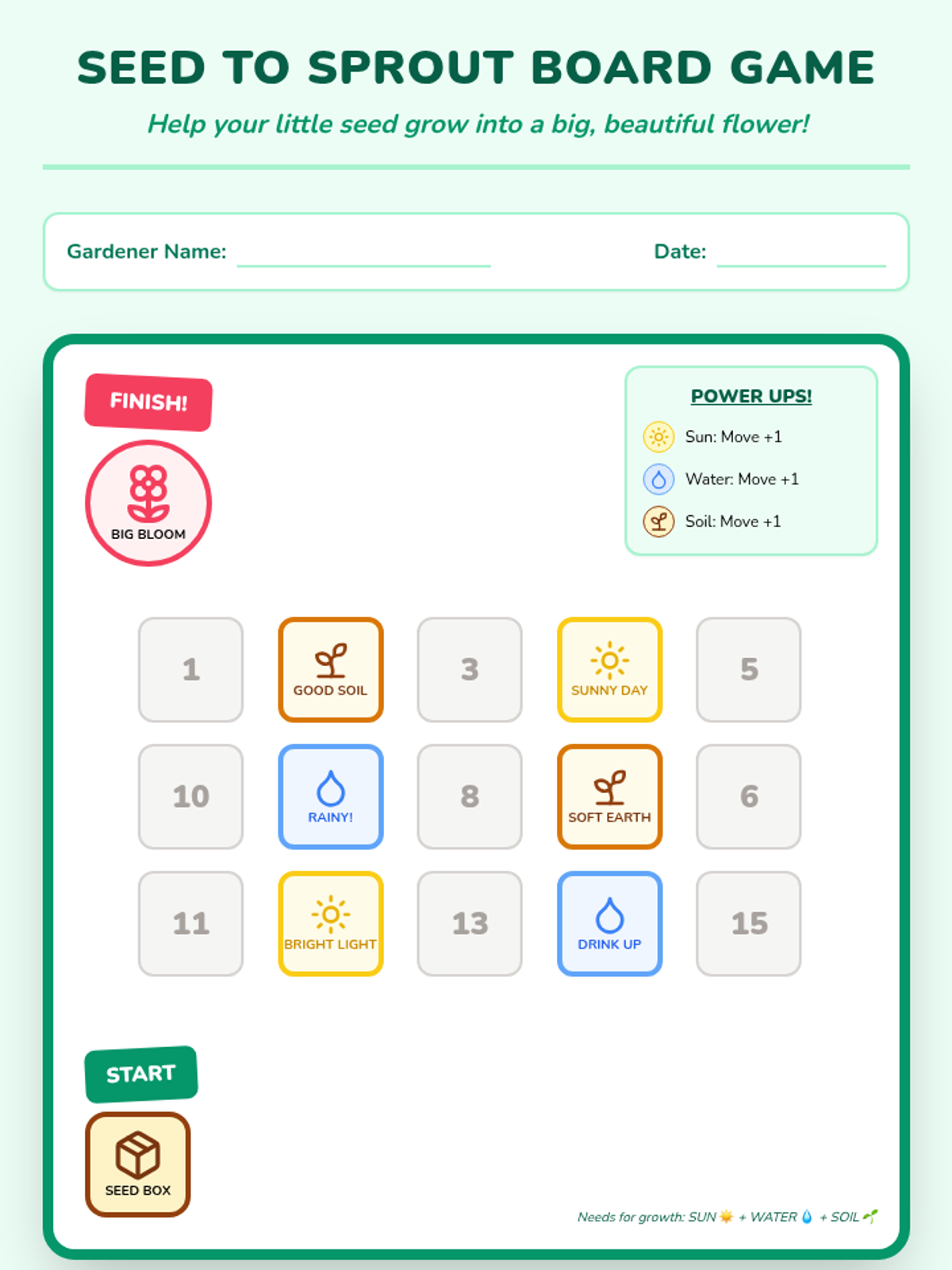
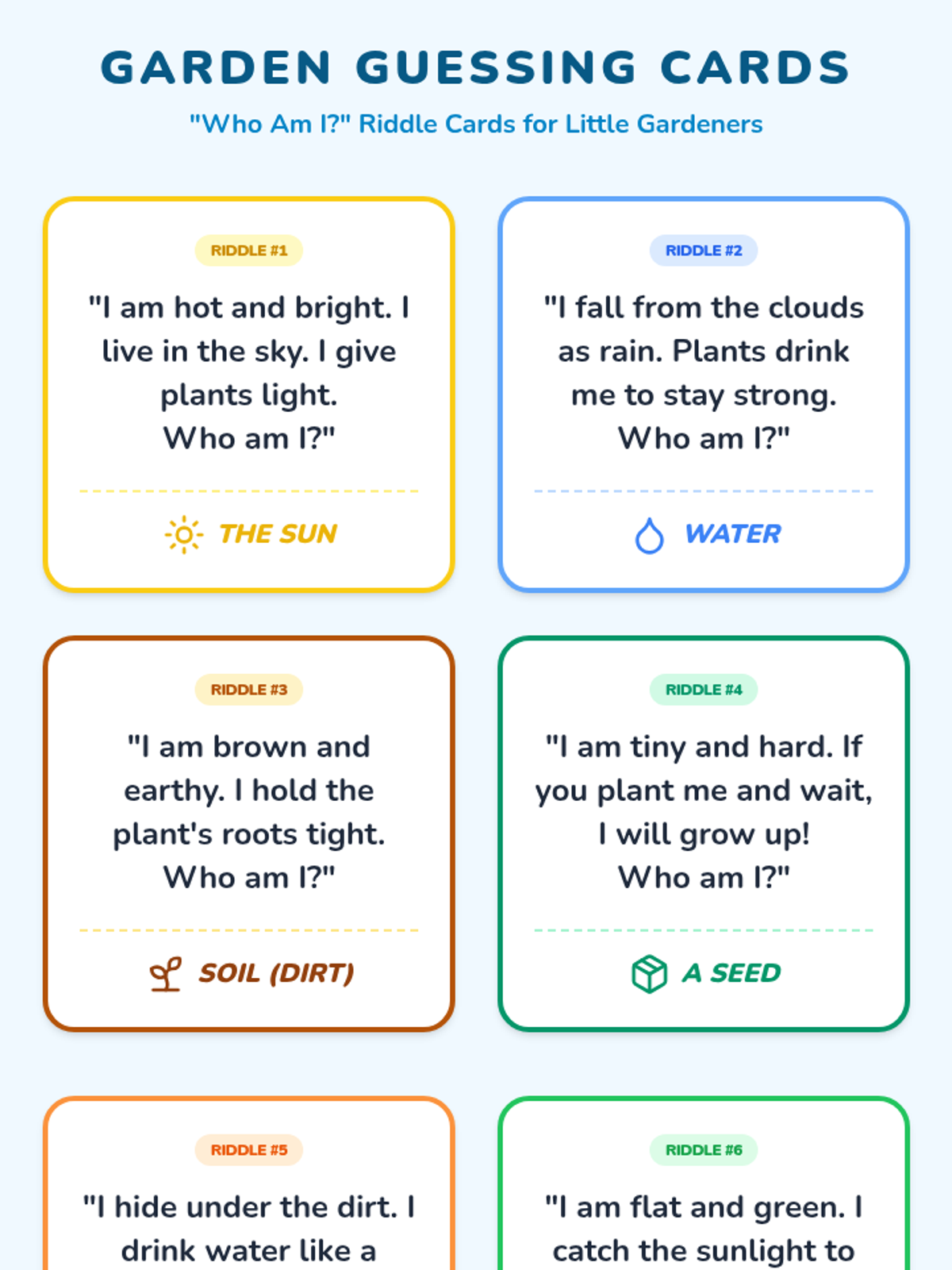
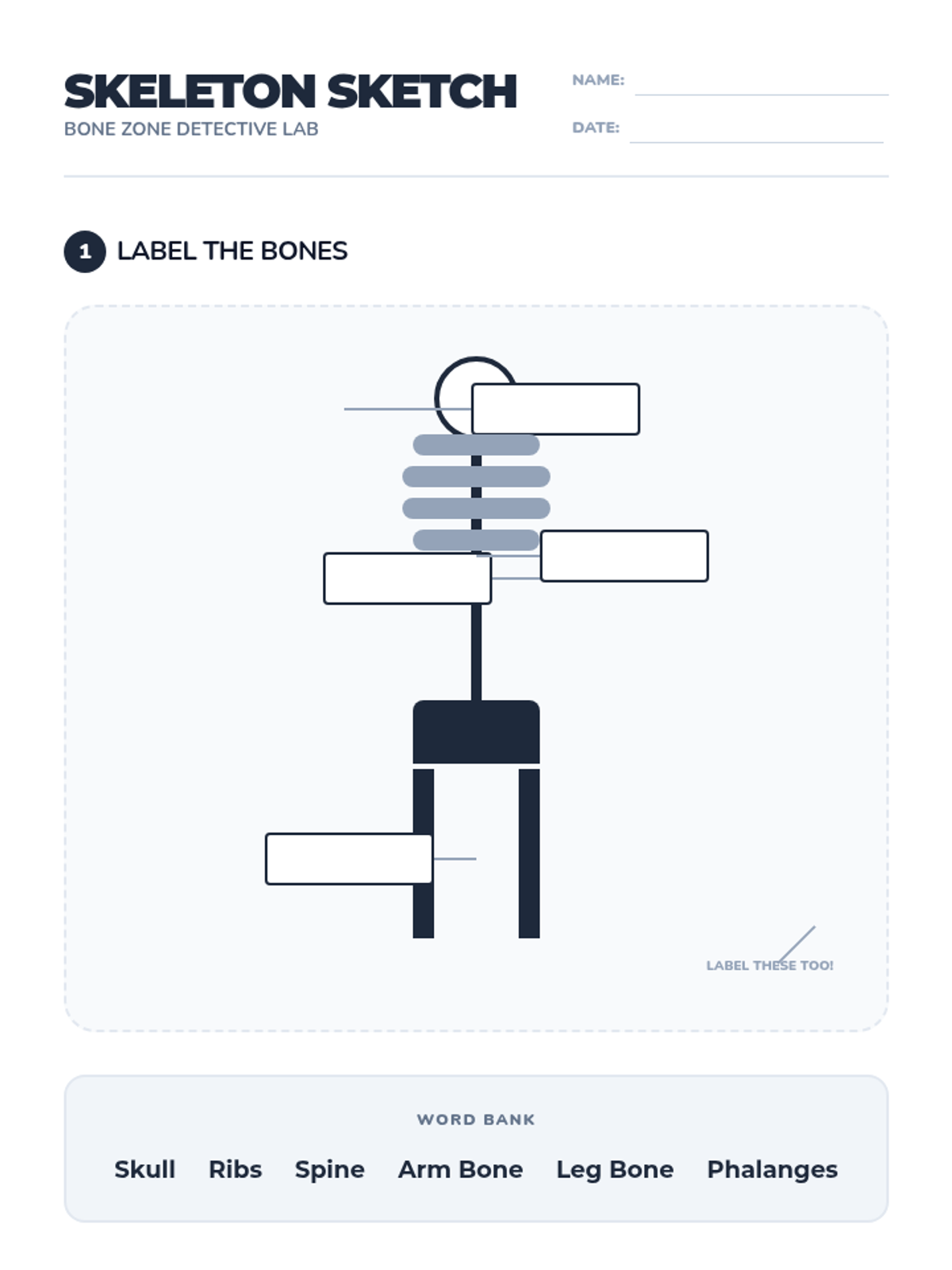
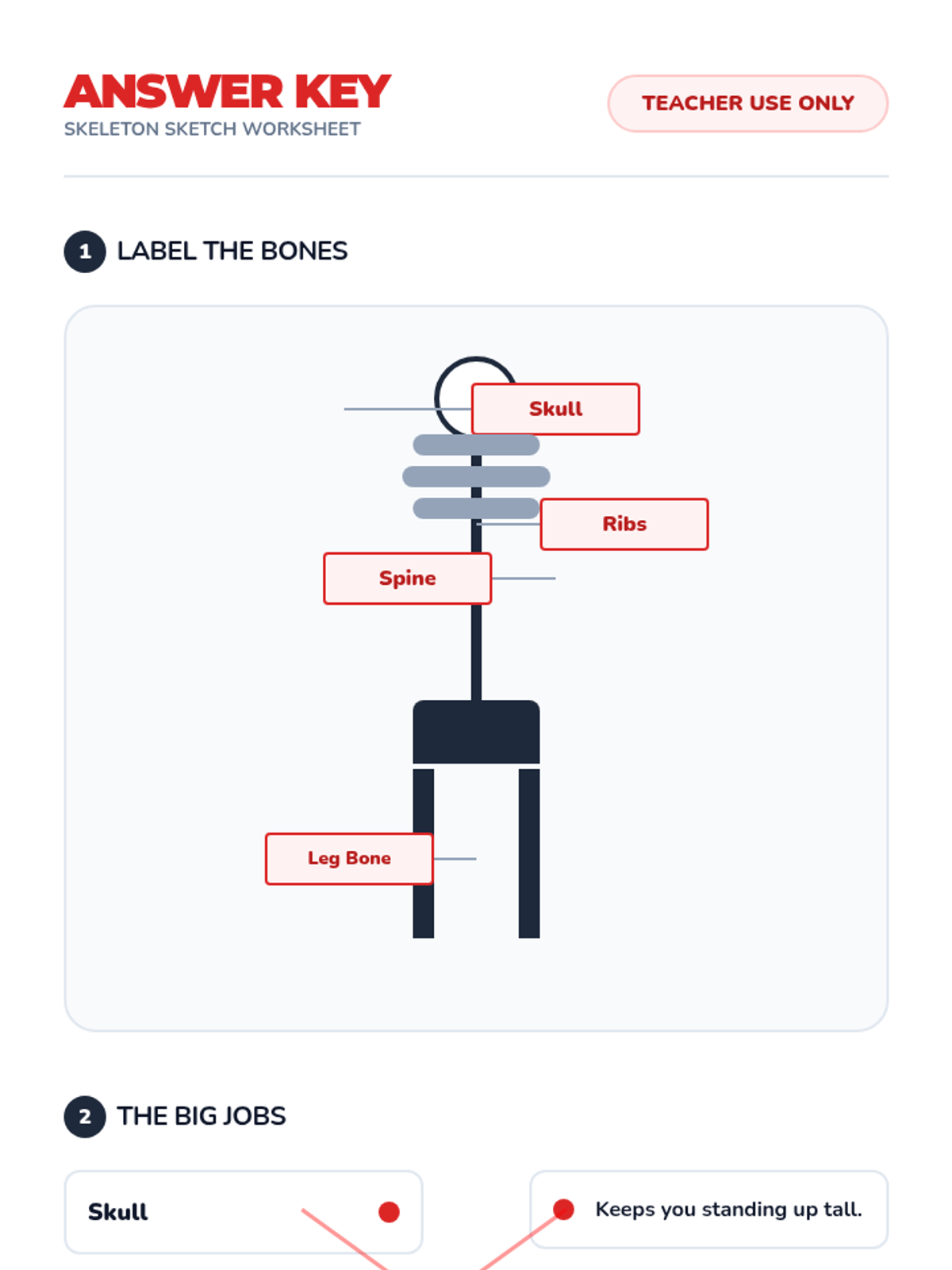
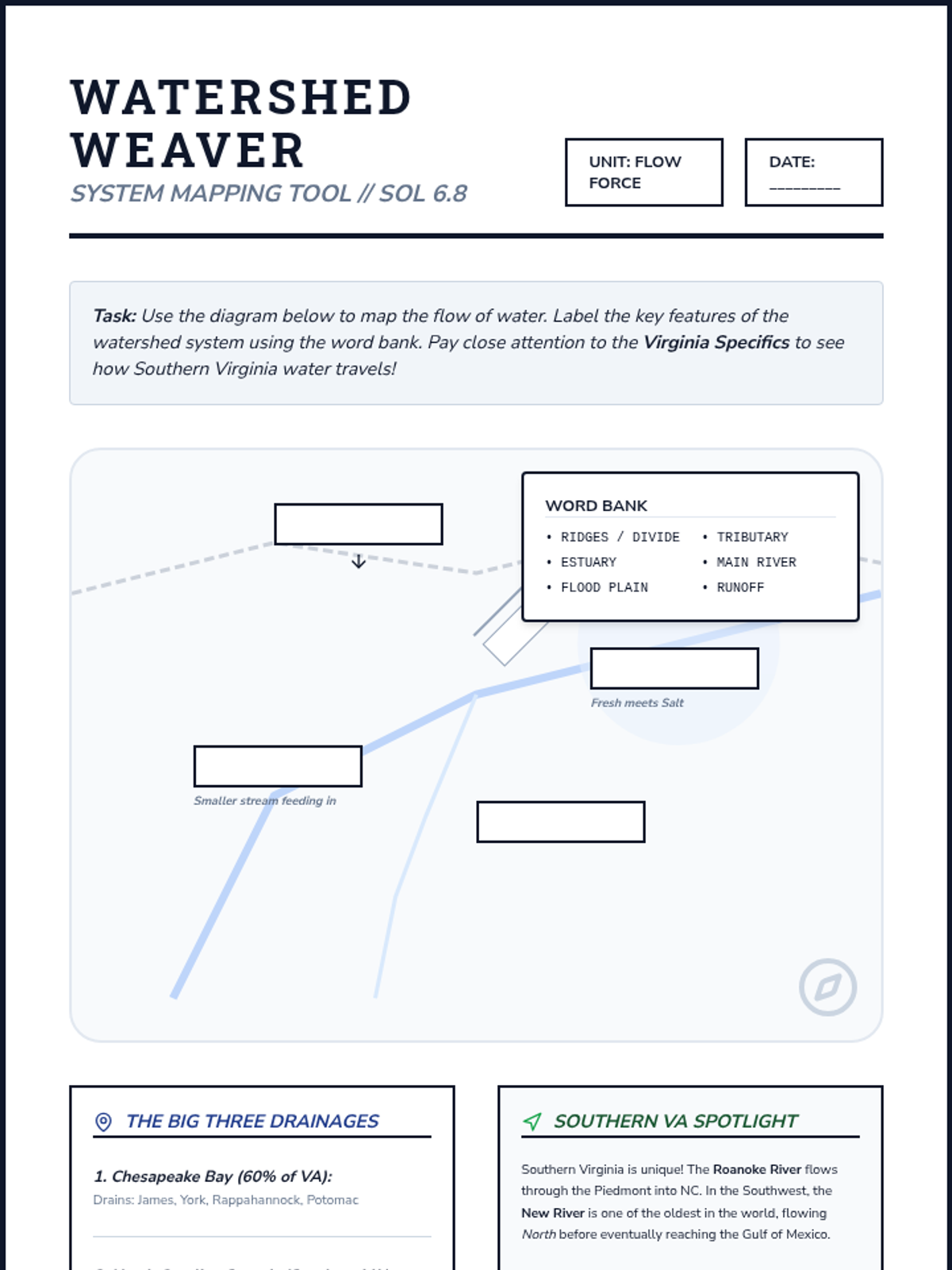
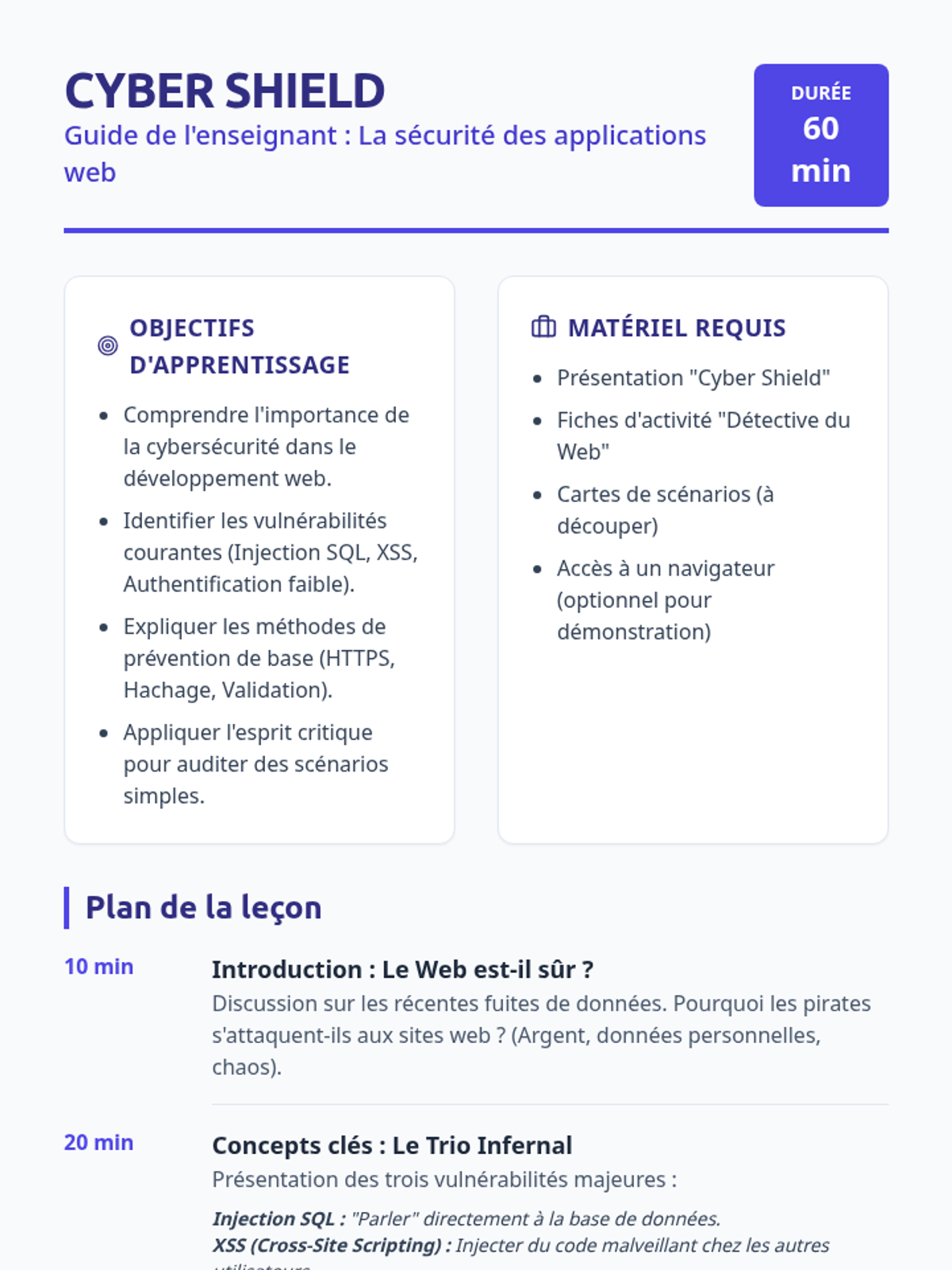
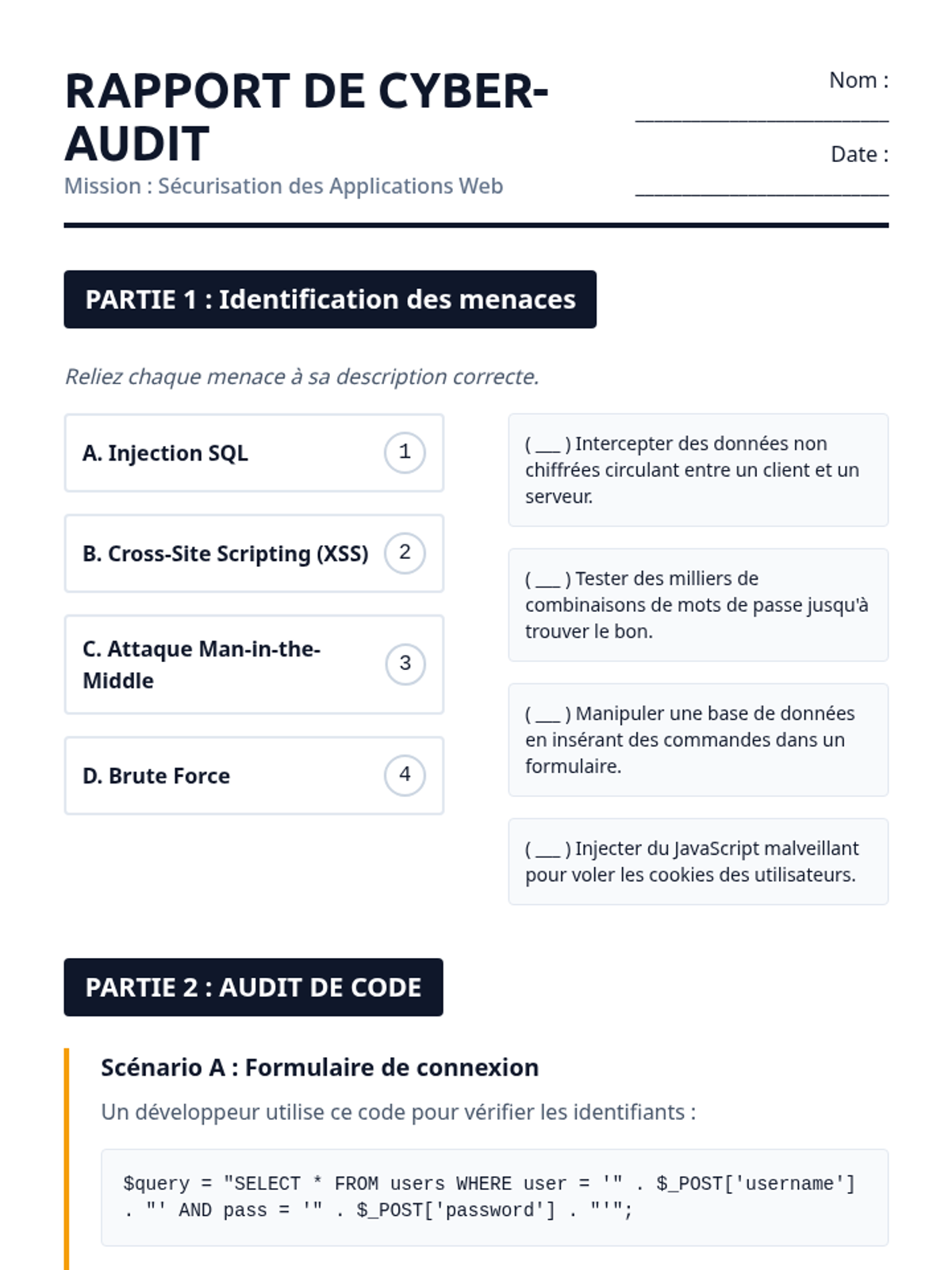
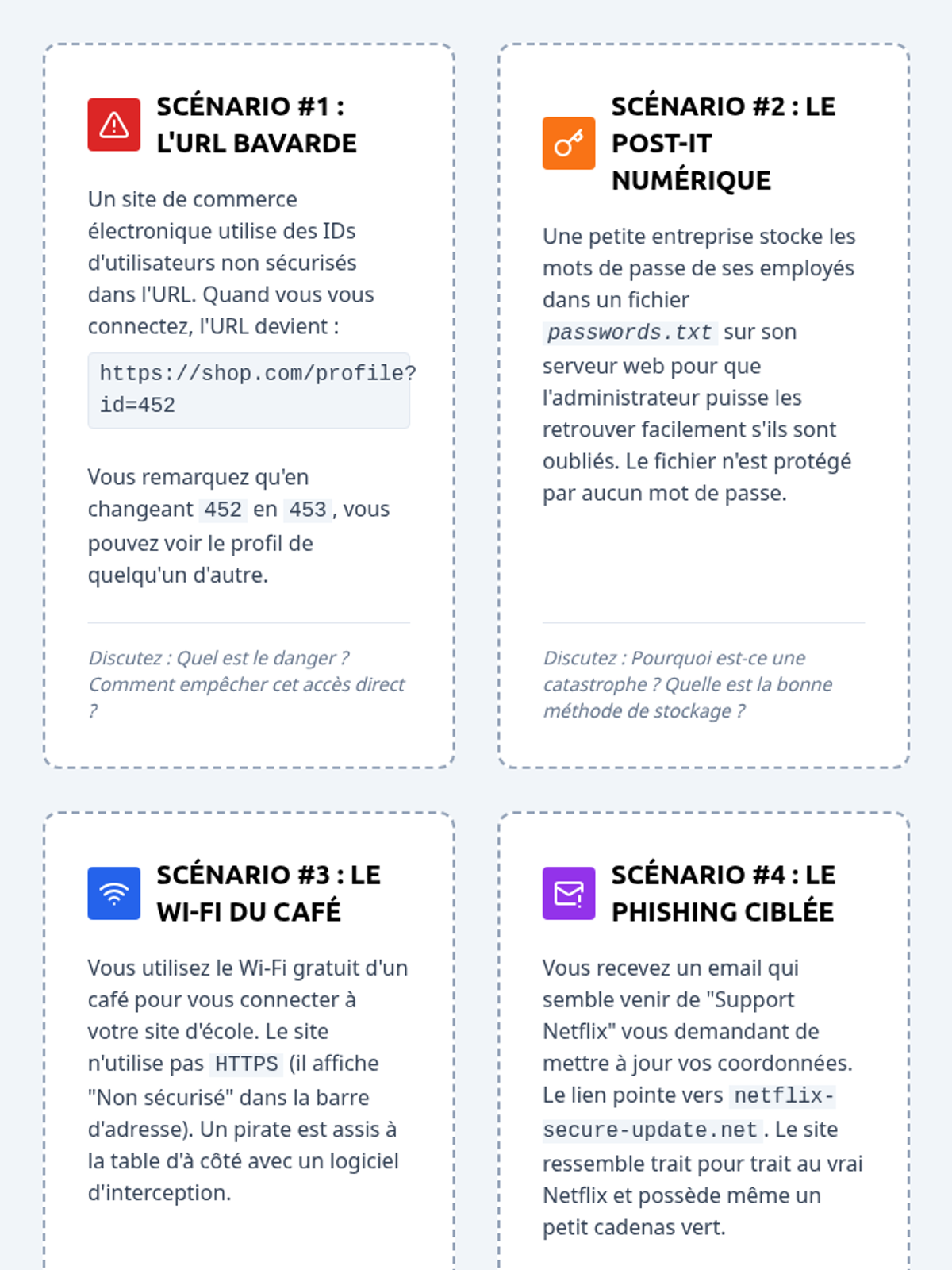
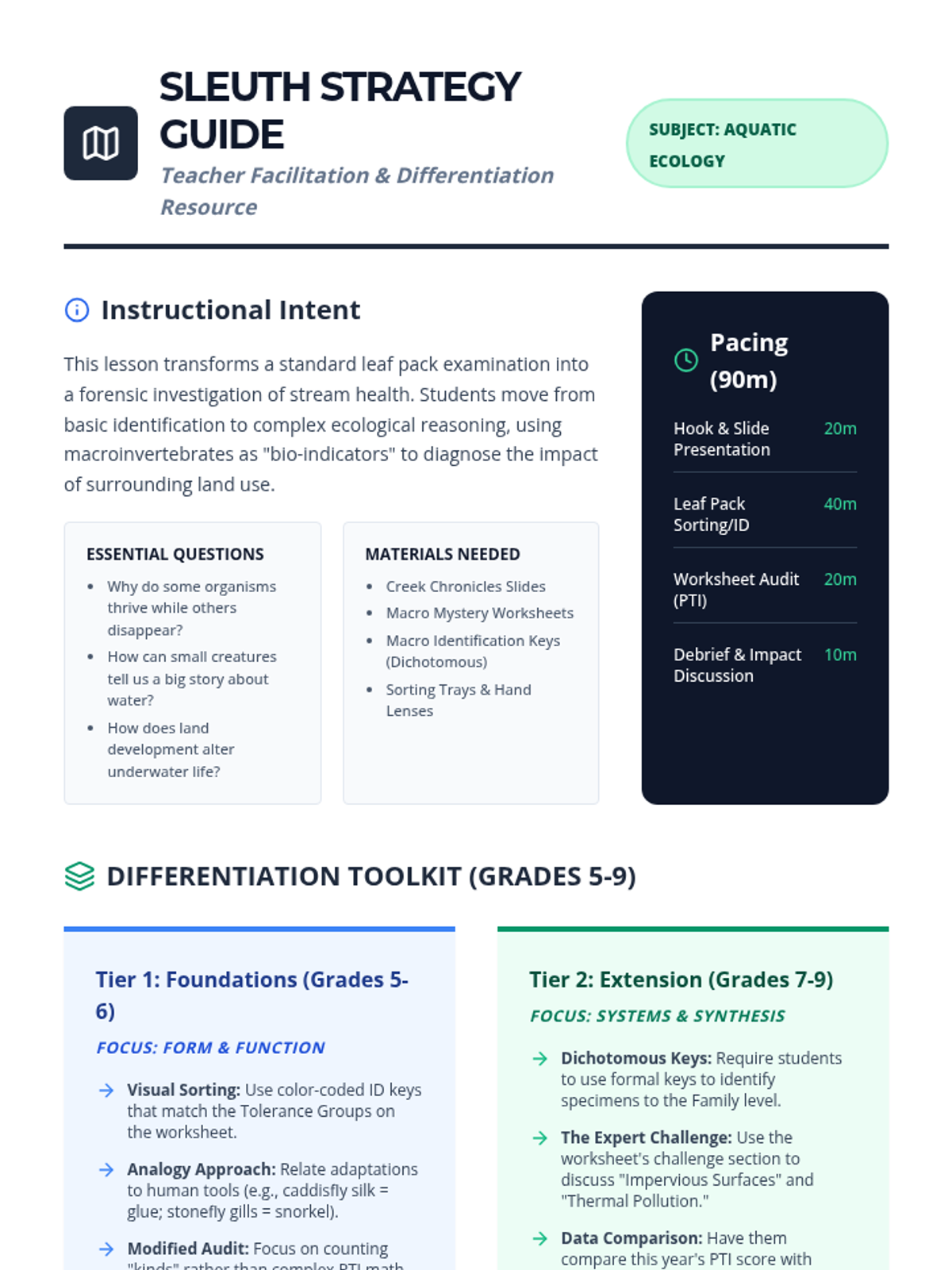
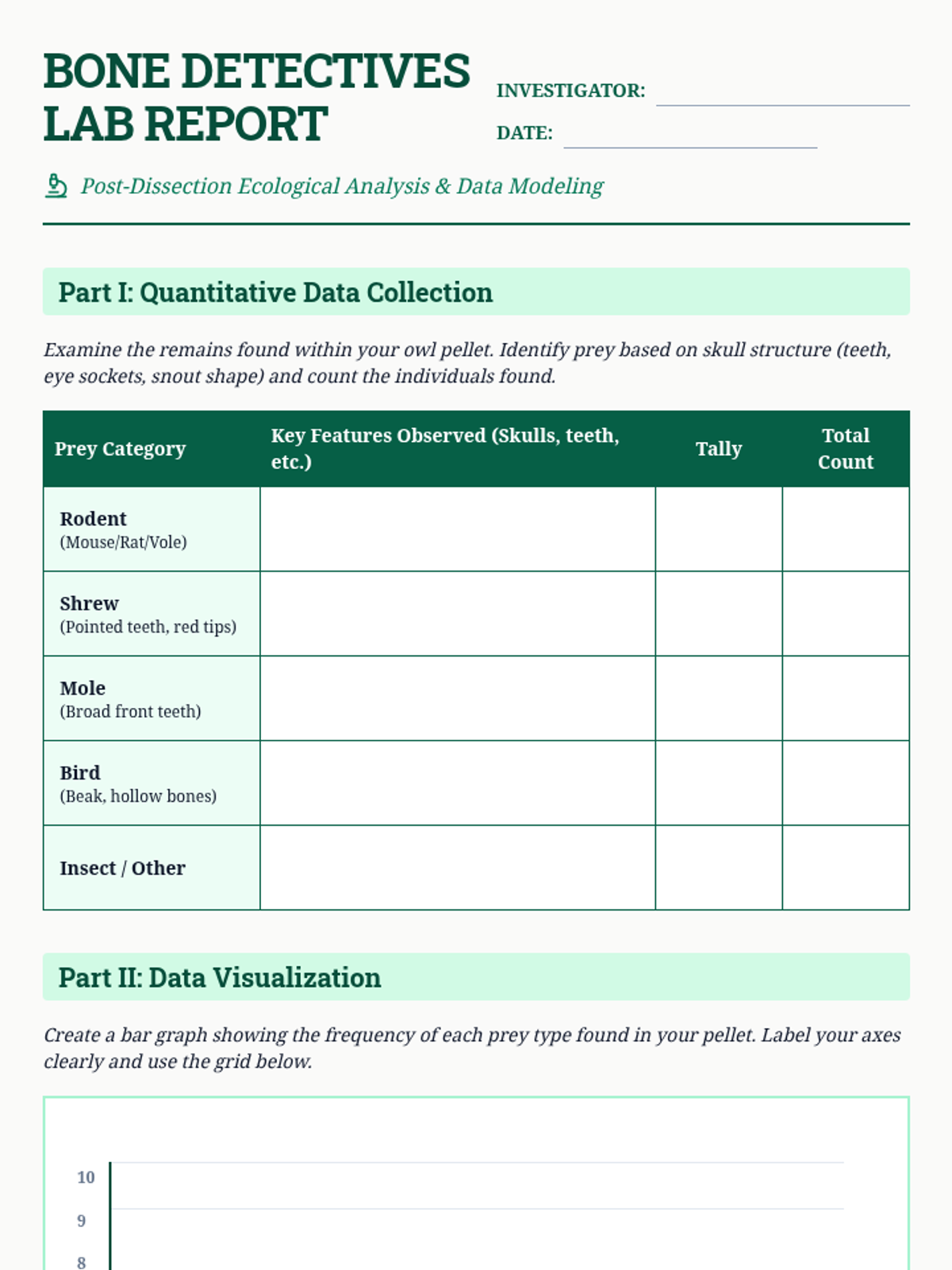
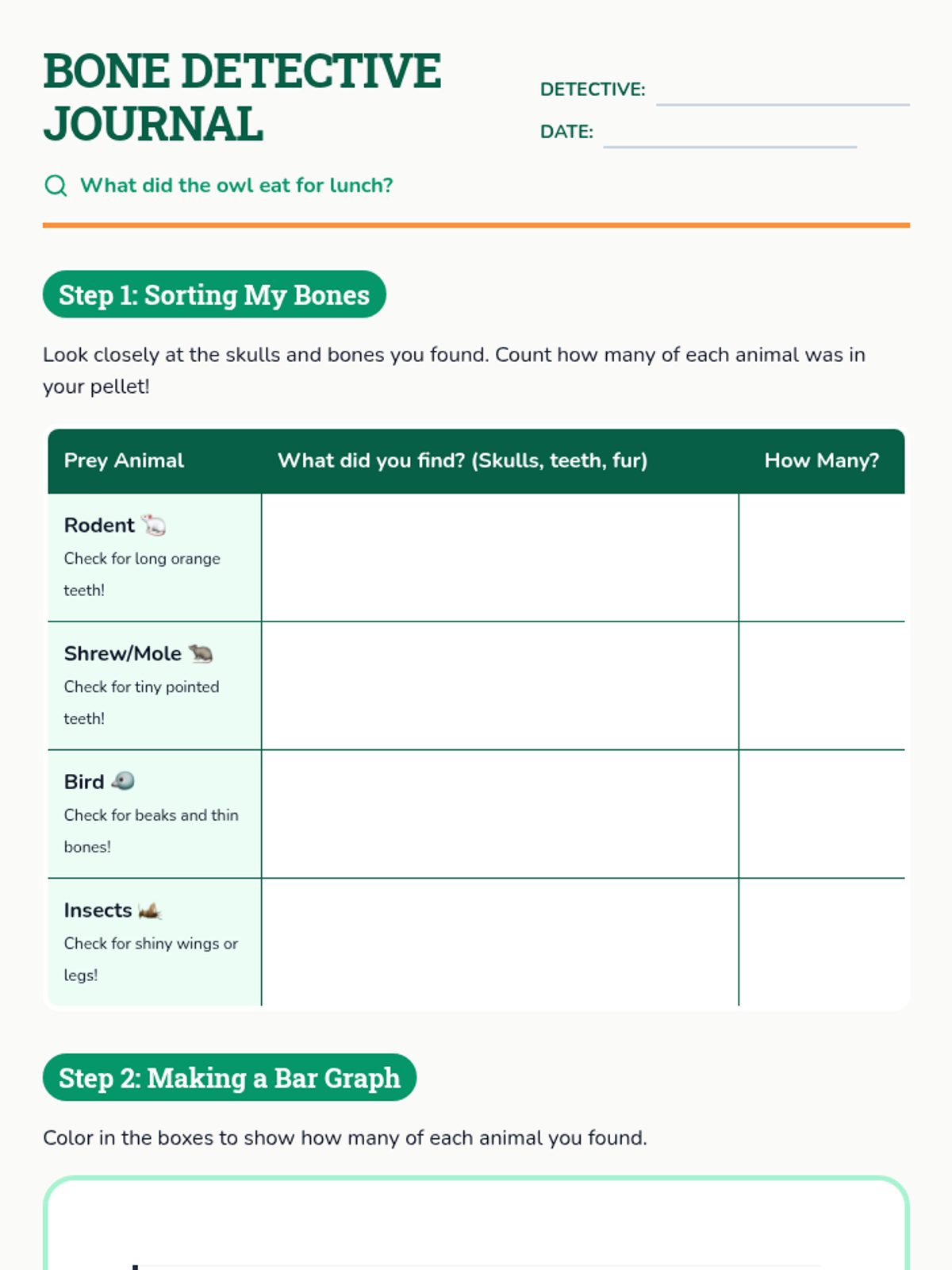
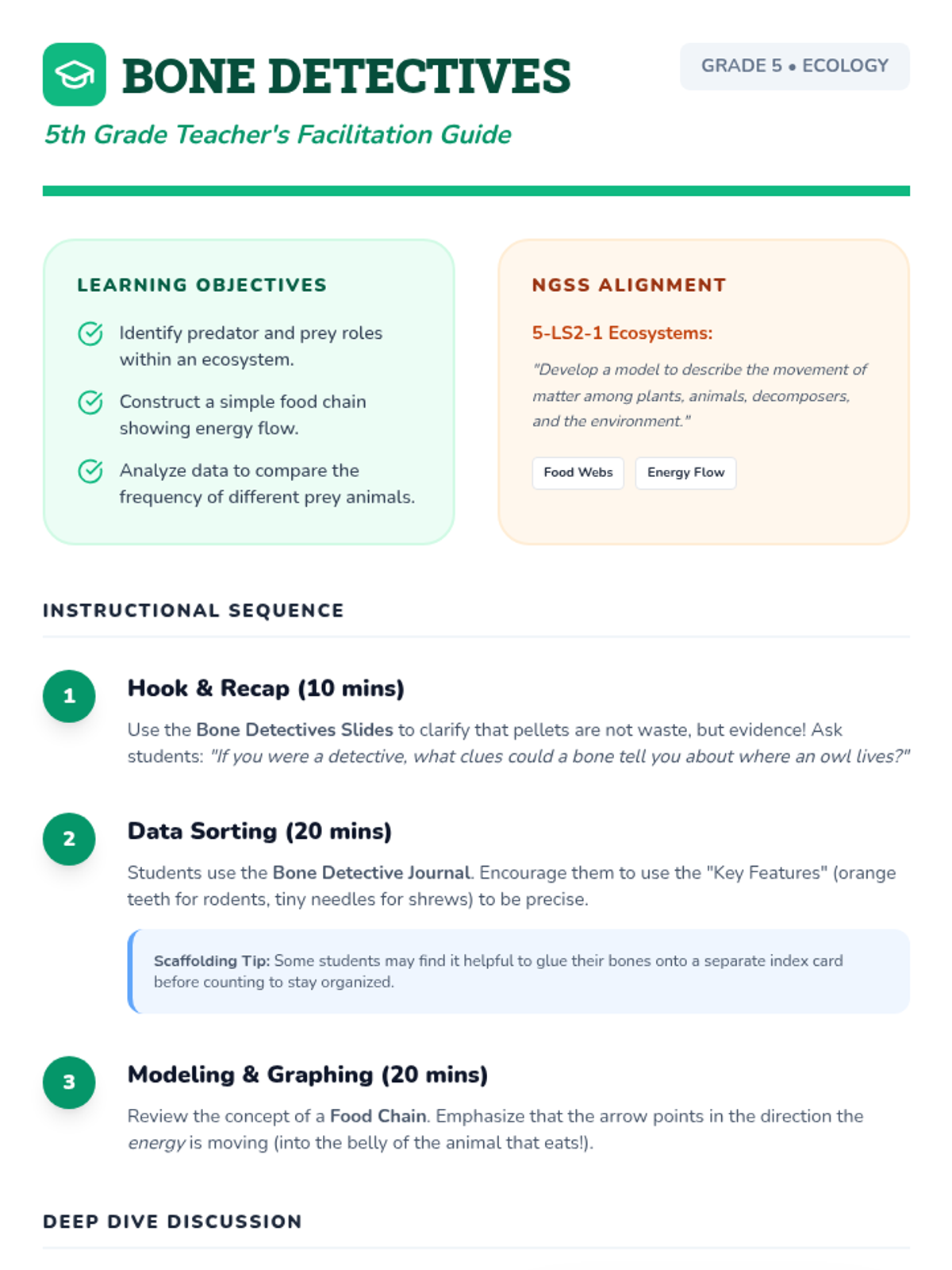
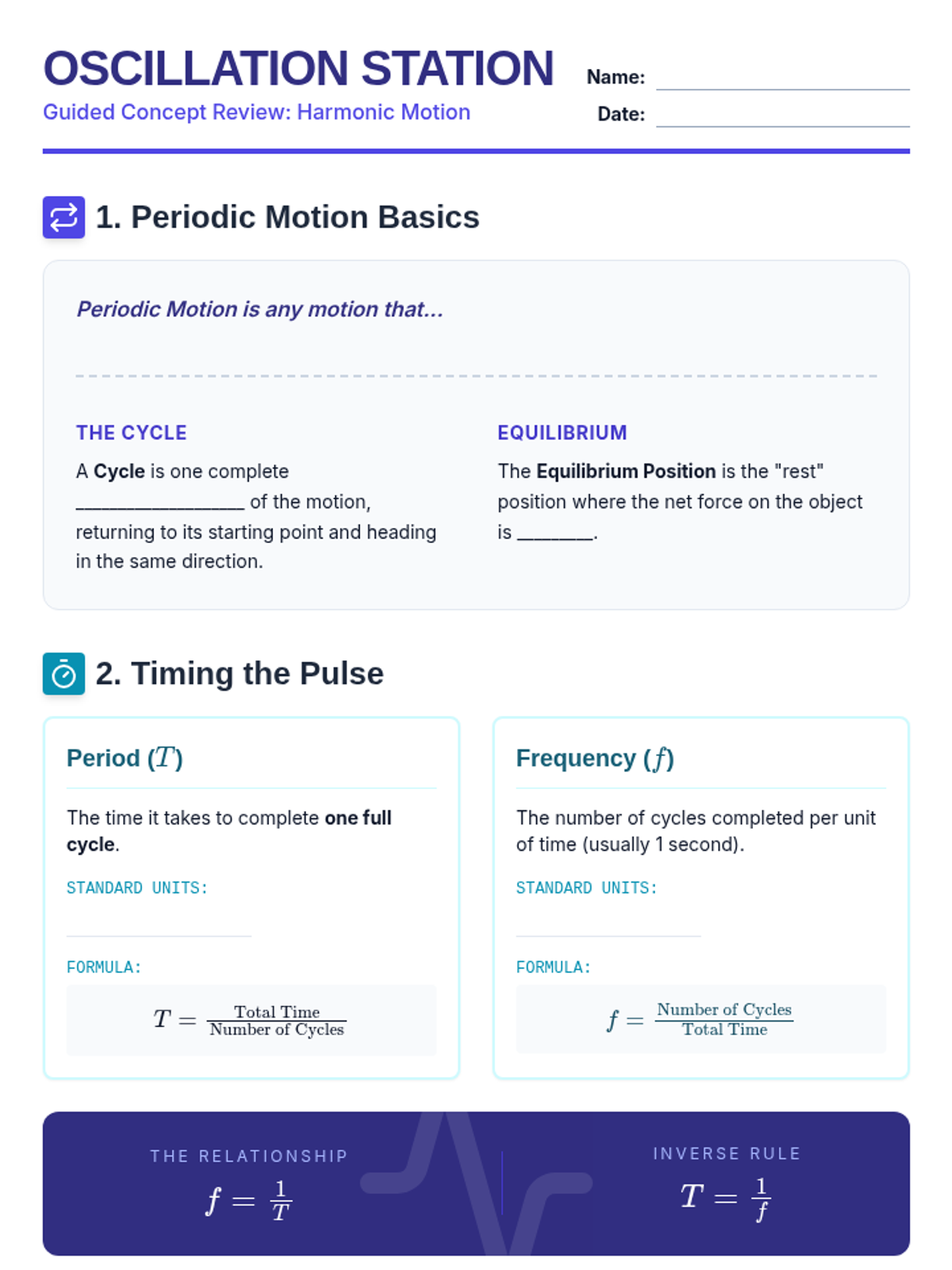
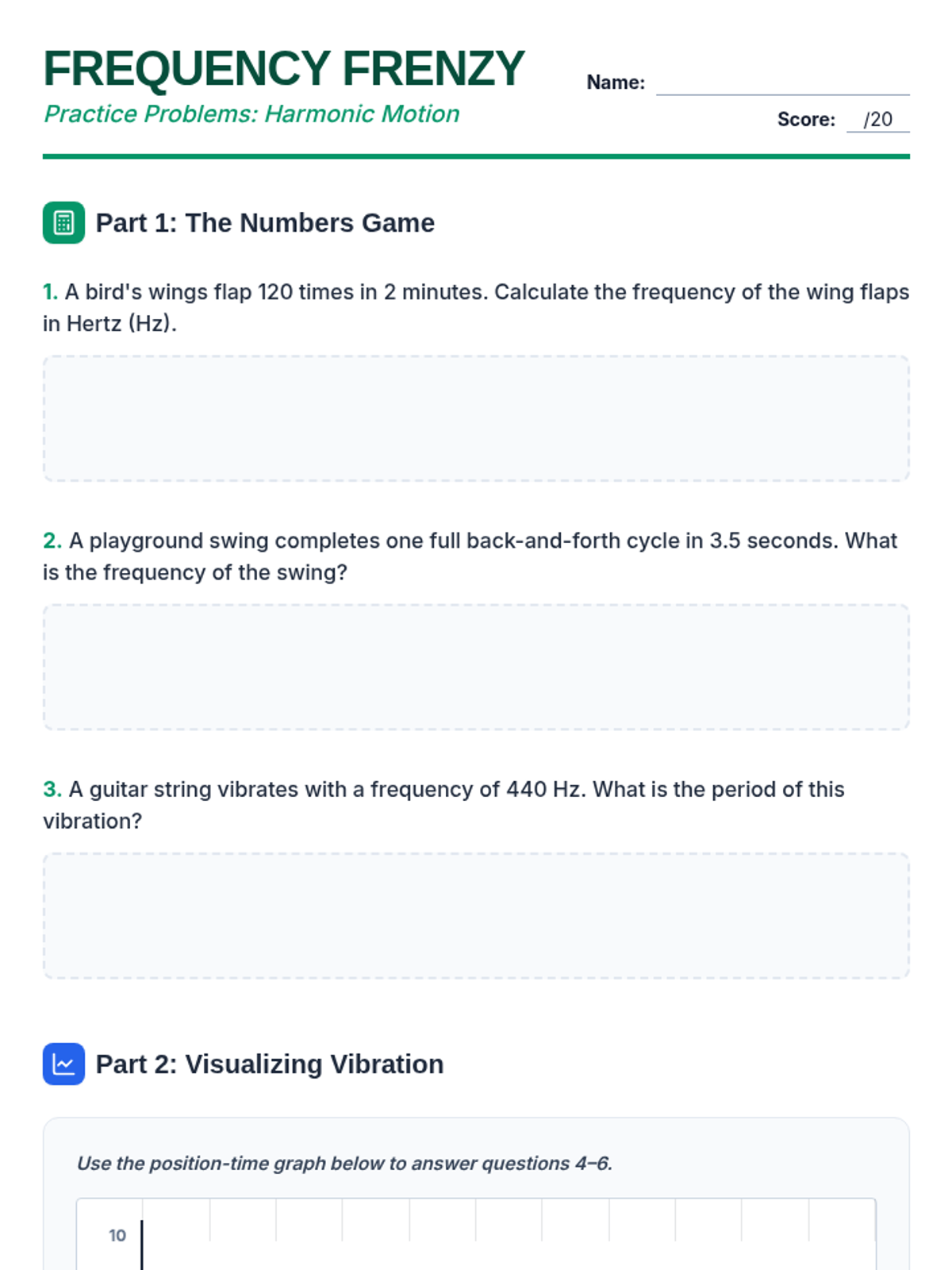
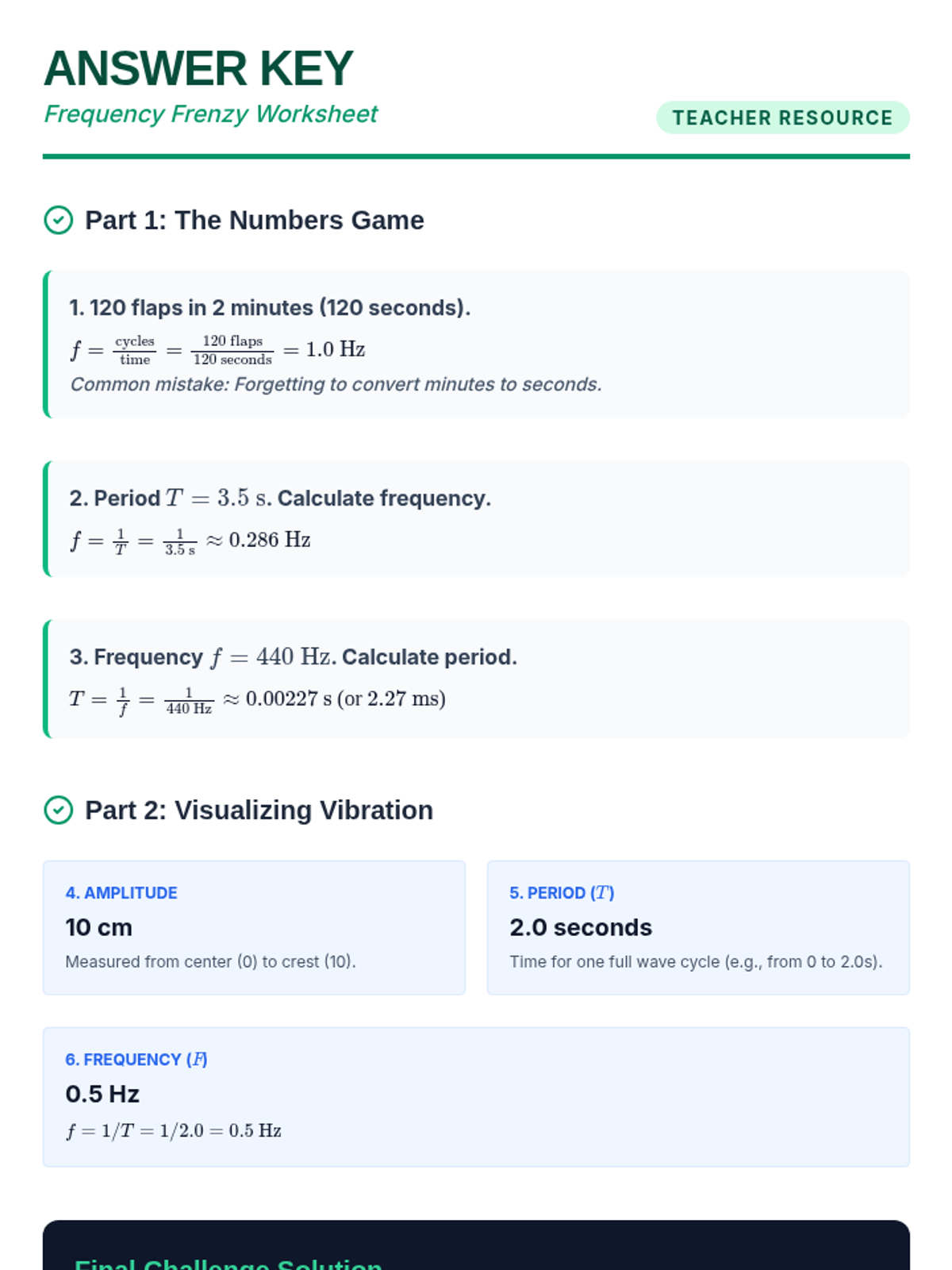
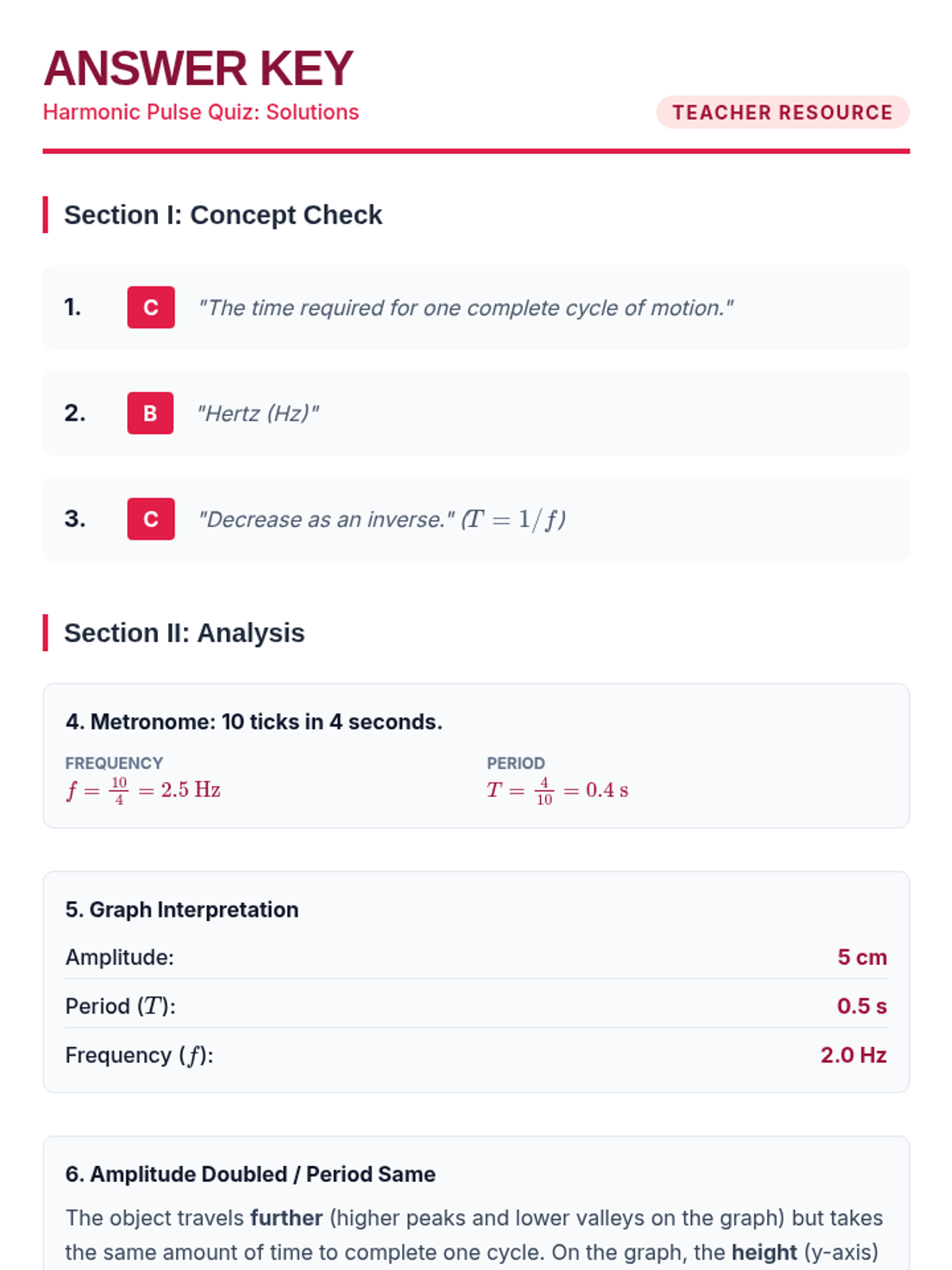
Examine critical smart contract vulnerabilities including reentrancy and arithmetic overflows. Students analyze the historic DAO hack, write exploit scripts in a controlled environment, and implement the 'Checks-Effects-Interactions' pattern to secure code.